
Beating IT Risks
.pdf174 |
IT service providers and vendors |
|
|
should be grounded in an analytical framework with a level of accuracy substantially better than the order-of-magnitude cost or quality improvements sought through undertaking it.
You should be aware that service providers confronted with a poor benchmarking report will probably dispute it and seek to obfuscate the results. If you can cut through that, the real issues may emerge – it may be difficult for the service provider to see how their prices can be cut or service lifted without their margins being impacted.
Managing multiple IT service providers
Most companies use multiple IT service providers,65 creating a patchwork quilt that unfortunately often evolves away from a pattern. While each service provider arrangement individually needs to be managed according to an overarching sourcing strategy (Aubert et al., 2004), and through the lifecycle from both contractual and relationship perspectives (Lacity and Hirschheim, 1993; Aalders, 2001), engaging with multiple providers creates a set of additional risks that need to be managed.
The rationale behind a multi-sourcing approach is to engage with the ‘best-of- breed’ for each job. That is, the most capable and effective at the right price, recognizing that no one provider can be the ‘best-of-breed’ in each service line.
Multi-sourcing risks arise when the ‘best-of-breed’ benefits do not eventuate and become overshadowed by negatives, issues and overheads. These ‘negative synergies’ have three root causes:
1.Poorly shaped ‘clusters’ of IT services;
2.Misaligned technology and provider strategies; and
3.Broken processes end-to-end.
In each case it is necessary to understand and then tackle the root causes to avoid the major risks of multi-sourcing.
Shape the ‘clusters’ of IT services
The key principles of shaping ‘clusters’ of IT services are to:
•Give each service provider control and responsibility over a set of related technologies or platforms – most providers excel in service delivery on only a limited range;
65 Empirical research of IT outsourcing deals between 1991 and 1995 identified that selective outsourcing decisions had higher success rates than total outsourcing or total insourcing decisions (Lacity and Willcocks, 1998).
Managing multiple IT service providers |
175 |
|
|
•Group IT activities that relate to ‘build’ or ‘service development’ activities – those spanning the cycle from proposing a solution through to managing the implementation of a working technology service; and
•Group IT activities that relate to ‘run’ or ‘service delivery’ activities – control over day-to-day operations and service once it has been developed.
An iterative approach is required to take into account the capabilities of the incumbent and alternative credible service providers and to explore potential economies of scope or scale that may be achievable. The clusters are refined on the basis of what the market has the capability to deliver, and where there is contestability.
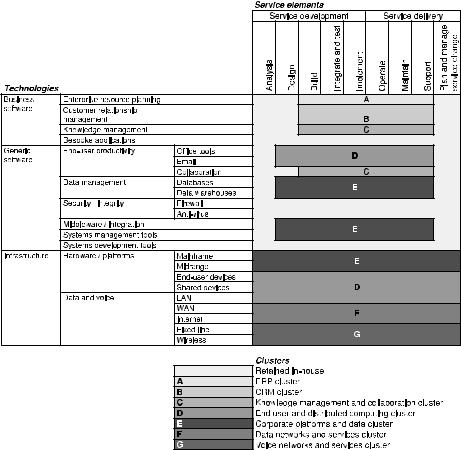
An example illustrates this shaping process (see Figure 7.1). Seven clusters of IT services that are candidates for external service providers are defined,
Figure 7.1—Recommended clustering of outsource arrangements
176 |
IT service providers and vendors |
|
|
spanning all technologies and IT activities, with a significant retained function holding responsibility for those activities not suitable for external service providers.
Further complexity may be introduced into the shaping of clusters for companies operating in multiple geographies or with diverse business units each with certain unique IT service needs.
Align technology strategies with sourcing strategies
Where companies have opened up competition in IT sourcing and then taken a hands-off approach to setting the technology agenda, the result can be a large number of tactical point solutions based on divergent technologies. These may each represent individually expedient deals but, when considered end-to-end, result in a poor overall service solution for the enterprise in the long term. Maintaining and supporting multiple generations of diverse technologies can become risky, complex and costly.
Before engaging in multi-sourcing it is important to resolve any such misalignment between technology and sourcing strategies. Any technology diversity should be for business reasons alone, with clearly defined technology standards agreed and enforced, and managed with an understanding of the link between IT products and the supply community, to deliver the maximum benefits.
Link processes end-to-end
The integration and alignment of multiple service provider efforts to achieve a high-quality end-to-end service is perhaps the greatest challenge of the multisourcing approach. Introducing a management and process framework as part of the contract early in the multi-source process, ideally at the time of real competition, provides a foundation for open cooperation and partnership relationships (Kern and Willcocks, 2000).
Clarifying the roles, responsibilities and hand-offs at the interfaces between service providers will help to avoid overlaps, disconnects, duplication, gaps and delays in operating the processes. In addition to day-to-day service delivery processes it is important that the management layers of the multiple service providers work effectively together and with your organization.
New and emerging risks in IT service provision
As new IT sourcing models evolve so do the risks. Two notable trends in recent years have been observed:
New and emerging risks in IT service provision |
177 |
|
|
1.The rise in the offshore IT service provider market.
2.The shift to a community-based model of support for open source software.
A brief exploration of these new and emerging sourcing models is set out below with suggestions as to how management attention may need to be heightened in each case.
Offshore sourcing
Offshore sourcing describes a model where the service provider’s base (where most of the work is carried out) is in a country different from your business. Most typically the service provider will be based in a country such as India that enjoys relative stability, lower costs than most Western countries and a relatively high IT service quality reputation.
The main risks to avoid that relate to offshore IT sourcing include:
•Political and economic instability may create a relatively less secure and predictable operating environment than exists for an on-shore provider;
•Inability of both service provider and customer teams to bridge social, language and cultural barriers to interface and to work as teams effectively on business initiatives that require IT solutions and services;66
•Difficulties achieving redress in the event of a contractual or service delivery dispute;
•Significant ‘hidden costs’ in terms of management time and the two-way ‘exchange’ costs of travel and accommodation;
•Legal and regulatory issues and requirements that you may not be able to satisfy by having your company data stored in another country; and
•Greater potential for your intellectual property tied up in the computer systems you use to be exploited by a third party in another country without an opportunity for redress.
The areas for heightened management awareness include:
•Sourcing strategy – include offshore sourcing considerations and be wary of pushing services to where they don’t naturally fit;
•Evaluation – include country-specific issues in the evaluation of service providers, specifically check: language, government support, legal and commercial environment, educational system, labour pool and skills, political stability, cultural issues and infrastructure that will support the provider’s ability to deliver services over the long term;
66 Lander et al. (2004) consider the trust-building mechanisms utilized in outsourced IT development projects.
178 |
IT service providers and vendors |
|
|
•Transition – invest in establishing the relationships and processes, in particular the interfaces at the ‘front end’ of IT service development (getting the business requirements right) and the ‘back end’ (rigorously testing the delivered solution);67 and
•Management – establish specific roles within the retained function to monitor review and control the performance of the service provider. Staff these roles with people skilled in ‘cross-boundary’ management.
Open-source software support
If managing service providers and vendors is difficult – can you do without them?
Open-source software is not owned and supported by a single service provider and there is no vendor, only the distributor. The source code (that is readable by programmers) is accessible to anyone and in theory can be supported by anyone. A so-called community model of support is relied upon for those who encounter problems. While the lock-in risks associated with proprietary IT products and services are avoided under the open-source model, there are additional risks.
The main risks to avoid that relate to open-source software support are:
•Difficulty interfacing with the open-source community for support – the process can appear complex and uncertain to those accustomed to phoning service provider and vendor hotlines;
•Difficulty securing SLAs for support of software – even when you are willing to pay;
•Uncertainty over the size of the installed and supported user base – are you part of a critical mass of customers for a software product that has real potential or do you risk being one of the few real users of what is principally a laboratory project;
•Lack of protection from intellectual property challenges brought against the user base of open-source software; and
•Uncertainty over upgrade paths and potential significant divergence and ‘fracturing’ of the open-source community, with each branch introducing a risk that you are left out of the mainstream.
The areas for heightened management awareness include:
•Sourcing strategy – carefully select the technologies and platforms suitable for an open-source community support (and/or self-support) model;
67 Sabherwal (2003) considers the evolution of coordination in outsourced software development projects.

Health check |
179 |
|
|
•Evaluation – confirm the strength of the open-source community for the products you wish to use;
•Transition – invest in building links into the open-source community; and
•Management – establish specific watching-brief roles for open-source within the retained technology strategy and planning function.
Health check
This section assists you consider at a macro-level the company’s IT service provider risk health, for input into the IT risk portfolio assessment.
Is this important to your business?
•IT service providers are relied on to support the running of a significant part of your business day-to-day.
•Critical IT services are dependent on IT components that aren’t fully supported in-house but are reliant on third party support.
•A material investment would be required if a single major IT service provider you rely on were to go under or a specific technology vendor discontinue a product line that you rely on.
If you agree with two or more of the three statements, then IT service provider risks are important to your business.
Are you doing the right things?
•All important systems are covered by current support and maintenance agreements with vendors.
•Service providers are delivering to their service level agreements.
•Contractual disputes with service providers are resolved adequately.
•An IT sourcing strategy is agreed with the business units that rely on IT services being developed and delivered.
If you agree with these statements, then you are doing the right things in your organization. If you disagree with two or more of the four statements, then there is significant room for improvement in your IT service provider risk management capability.

180 |
IT service providers and vendors |
|
|
Do you have a good track record?
•Service providers deliver the necessary support to your major IT projects.
•Business disruption due to service provider failure to deliver day-to-day has been rare and tolerable.
•We have been able to exit and transition out of service provider agreements that were not working.
If you agree with these statements, then you have a good track record of managing IT service provider risks. If you disagree with one or more of the three statements, then there is evidence of the need to improve IT risk management capability.
Case study: Financial services
Delivering a business-responsive IT infrastructure for less
This US-based financial services business offers its clients a comprehensive array of financial products and services, including life insurance, fixed and variable annuities, defined contribution retirement plans and mutual funds.
In a fundamental re-examination of their approach to the delivery of IT infrastructure services, the options for outsourcing and the challenge of undertaking a major transformation were considered in parallel.
Their starting point was to recognize that in transactional outsourcing, the focus on ‘getting the best deal’ has resulted in many outsourcing failures. The consequences of ‘winning’ in the deal, and ‘losing’ in the future implementation were clearly unacceptable.
Therefore, the business sought a transformational agreement with an outsource provider and focused initially on defining a robust governance model for the current and future relationship. The governance model was developed based on an understanding of the service provider’s management approach, their operating style, and their use of process standards such as the Information Technology Infrastructure Library (ITIL). It also accepted the need for organizational change within the retained IT function; a new way of interacting with the business and the need for review and development of internal processes.
With the assistance of an independent delivery partner, the business:

Case study: Financial services |
181 |
|
|
•Conducted a diligent assessment of the insource versus outsource options in parallel with the engagement of potential service providers, establishing a robust business case that modelled the financial and risk implications for each sourcing option;
•Came to grips with and built in the necessary deal flexibility for the impact of new technology approaches, such as utility computing, within the context of the desired infrastructure transformation; and
•Designed the necessary organizational change and established a service management organization to oversee the transition and proactively manage the third party’s delivery performance ongoing, thereby mitigating major areas of operational risk.
A major agreement to outsource its IT infrastructure was executed. As the relationship emerges from transition, the business is well-placed to obtain three main benefits:
•To advance and simplify the regional technology infrastructure – improving stability, recoverability and security;
•To improve the cost structure – permitting a scaling of the infrastructure more easily with predictable cost impacts; and
•To enable the business transformation senior executives envisioned.
Printed with permission of PA Consulting Group
182 |
IT service providers and vendors |
|
|

8 Applications
When downtime means down time
The fourth major air traffic control breakdown in three years left more than 200 000 travellers fuming, with delays and cancellations snowballing from Southampton to Glasgow. For an hour at the height of the morning peak, a computer failure left planes barred from taking off at all major airports . . .
For airlines, the breakdown left planes, pilots and cabin crew in all the wrong places, with costs running into tens of millions of pounds . . .
According to National Air Traffic Services (NATS), problems began when engineers turned up at Heathrow’s West Drayton control centre before 3 am to test software which is intended to be introduced later in the summer. The 45-minute test appeared to go as planned. But when the system was switched back on to full operation at 6:03 am, ready for the arrival of the morning’s transatlantic traffic, controllers at NATS’ nerve centre in Swanwick, near Southampton, noticed ‘errors’ in flight data . . .
The spokesman admitted the system was 30 years old. (Guardian, 2004)
Lessons to be learned
In December 1999, RMIT commenced the Academic Management System (AMS) information technology implementation project. The aim of the AMS project was to integrate all RMIT’s student management activities into a consolidated system to streamline processes including student enrolments . . .
The implementation of the AMS was largely outsourced and went ‘live’ in October 2001. Since going ‘live’, the AMS has suffered a number of functional and technical problems . . .
The anticipated cost of implementation of the AMS to the end of 2003 of $47.2 million represents 3.7 times the original implementation budget. The current system has not provided the functionality originally planned and RMIT faces significant challenges in transitioning to a high quality student
