
- •Contents
- •List of Figures
- •List of Tables
- •About the Author
- •Acknowledgements
- •Abbreviations
- •Introduction
- •1 Hardware Design
- •1.1 Separation of Routing and Forwarding Functionality
- •1.2 Building Blocks
- •1.2.1 Control Module
- •1.2.2 Forwarding Module
- •1.2.4 Stateful Failover
- •1.3 To Flow or Not to Flow?
- •1.4 Hardware Redundancy, Single Chassis or Multi Chassis
- •2 Transport Media
- •2.1 Maximum Transmission Unit (MTU)
- •2.1.1 Path MTU Discovery
- •2.1.2 Port Density
- •2.1.3 Channelized Interfaces
- •2.2 Ethernet
- •2.2.1 Address Resolution Protocol (ARP)
- •2.3 Asynchronous Transfer Mode (ATM)
- •2.4 Packet Over SONET (POS)
- •2.5.1 Intelligent Protection Switching
- •2.6 (Fractional) E1/T1/E3/T3
- •2.7 Wireless Transport
- •2.7.1 Regulatory Constraints
- •2.7.2 Interference
- •2.7.3 Obstructions
- •2.7.4 Atmospheric Conditions
- •3.1.1 Management Ethernet
- •3.1.2 Console Port
- •3.1.3 Auxiliary (Aux) Port
- •3.1.4 Remote Power Management
- •3.1.5 Uninterruptible Power Supplies (UPS)
- •3.2 Network Time Protocol (NTP)
- •3.3 Logging
- •3.4 Simple Network Management Protocol (SNMP)
- •3.4.1 SNMPv1, v2c and v3
- •3.5 Remote Monitoring (RMON)
- •3.6 Network Management Systems
- •3.6.1 CiscoWorks
- •3.6.2 JUNOScope
- •3.7.1 Concurrent Version System (CVS)
- •3.8 To Upgrade or Not to Upgrade
- •3.8.1 Software Release Cycles
- •3.9 Capacity Planning Techniques
- •4 Network Security
- •4.1 Securing Access to Your Network Devices
- •4.1.1 Physical Security
- •4.1.2 Authentication, Authorization and Accounting (AAA)
- •4.2 Securing Access to the Network Infrastructure
- •4.2.1 Authentication of Users, Hosts and Servers
- •4.2.2 Encryption of Information
- •4.2.3 Access Tools and Protocols
- •4.2.4 IP Security (IPsec)
- •4.2.5 Access Control Lists
- •4.2.6 RFC 1918 Addresses
- •4.2.7 Preventing and Tracing Denial of Service (DoS) Attacks
- •5 Routing Protocols
- •5.1 Why Different Routing Protocols?
- •5.2 Interior Gateway Protocols (IGP)
- •5.2.1 Open Shortest Path First (OSPF)
- •5.2.2 Authentication of OSPF
- •5.2.3 Stub Areas, Not So Stubby Areas (NSSA) and Totally Stubby Areas
- •5.2.4 OSPF Graceful Restart
- •5.2.5 OSPFv3
- •5.2.8 IS-IS Graceful Restart
- •5.2.9 Routing Information Protocol (RIP)
- •5.2.10 Interior Gateway Routing Protocol (IGRP) and Enhanced Interior Gateway Routing Protocol (EIGRP)
- •5.2.11 Diffusing Update Algorithm (DUAL)
- •5.2.12 Stuck-in-Active
- •5.2.13 Why use EIGRP?
- •5.3 Exterior Protocols
- •5.3.1 Border Gateway Protocol (BGP)
- •5.3.2 Authentication of BGP
- •5.3.3 BGP Graceful Restart
- •5.3.4 Multiprotocol BGP
- •6 Routing Policy
- •6.1 What is Policy For?
- •6.1.1 Who Pays Whom?
- •6.2 Implementing Scalable Routing Policies
- •6.3 How is Policy Evaluated?
- •6.3.2 The Flow of Policy Evaluation
- •6.4 Policy Matches
- •6.5 Policy Actions
- •6.5.1 The Default Action
- •6.5.2 Accept/Permit, Reject/Deny, and Discard
- •6.6 Policy Elements
- •6.7 AS Paths
- •6.9 Internet Routing Registries
- •6.10 Communities
- •6.11 Multi-Exit Discriminator (MED)
- •6.12 Local Preference
- •6.13 Damping
- •6.14 Unicast Reverse Path Forwarding
- •6.15 Policy Routing/Filter-Based Forwarding
- •6.16 Policy Recommendations
- •6.16.1 Policy Recommendations for Customer Connections
- •6.16.2 Policy Recommendations for Peering Connections
- •6.16.3 Policy Recommendations for Transit Connections
- •6.17 Side Effects of Policy
- •7 Multiprotocol Label Switching (MPLS)
- •7.2 Label Distribution Protocols
- •7.3 Tag Distribution Protocol (TDP)
- •7.4 Label Distribution Protocol (LDP)
- •7.4.1 LDP Graceful Restart
- •7.5.1 RSVP-TE Graceful Restart
- •7.6 Fast Reroute
- •7.7 Integrating ATM and IP Networks
- •7.8 Generalized MPLS (GMPLS)
- •8 Virtual Private Networks (VPNs)
- •8.1 VPNs at Layer 3
- •8.1.1 Layer 3 VPN (RFC 2547bis)
- •8.1.2 Generic Router Encapsulation (GRE)
- •8.1.3 IPsec
- •8.2 VPNs at Layer 2
- •8.2.1 Circuit Cross-Connect (CCC)
- •8.2.3 Martini (Layer 2 circuits)
- •8.2.4 Virtual Private Wire Service (VPWS)
- •8.2.5 Virtual Private LAN Service (VPLS)
- •8.2.6 Layer 2 Tunnelling Protocol (L2TP)
- •9.1 Design and Architectural Issues of CoS/QoS
- •9.2 CoS/QoS Functional Elements
- •9.2.3 Congestion Avoidance Mechanisms
- •9.2.4 Queueing Strategies
- •9.3 QoS Marking Mechanisms
- •9.3.1 Layer 2 Marking
- •9.3.2 Layer 3 QoS
- •9.3.3 MPLS EXP
- •9.4 Integrating QoS at Layer 2, in IP and in MPLS
- •9.4.1 DiffServ Integration with MPLS
- •10 Multicast
- •10.1 Multicast Forwarding at Layer 2
- •10.1.1 Multicast on Ethernet and FDDI
- •10.1.2 Multicast Over Token Ring
- •10.1.3 Internet Group Management Protocol (IGMP)
- •10.1.4 IGMP Snooping
- •10.1.5 PIM/DVMRP Snooping
- •10.1.6 Immediate Leave Processing
- •10.1.7 Cisco Group Management Protocol (CGMP)
- •10.2 Multicast Routing
- •10.2.1 Reverse Path Forwarding (RPF) Check
- •10.2.2 Dense Mode Protocols
- •10.2.3 Sparse Mode Protocols
- •10.2.4 Multicast Source Discovery Protocol (MSDP)
- •10.2.5 Multiprotocol BGP
- •10.2.6 Multicast Scoping
- •11.1 Evolution and Revolution
- •11.2 IPv6 Headers
- •11.3 IPv6 Addressing
- •11.3.1 Hierarchical Allocations
- •11.3.2 Address Classes
- •11.5 Domain Name System (DNS)
- •11.6 Transition Mechanisms
- •11.6.1 Dual Stack
- •11.6.3 Tunnelling IPv6 in IPv4
- •11.7 Routing in IPv6
- •11.7.2 OSPFv3
- •11.7.3 RIPng
- •11.7.4 Multiprotocol BGP
- •11.8 Multicast in IPv6
- •11.9 IPv6 Security
- •11.10 Mobility in IPv6
- •References
- •Index

7.6 FAST REROUTE |
103 |
populate the TED, which is used by the CSPF process to calculate the path of the LSP. The same extended information types are carried by IS-IS as are carried with OSPF.
7.6FAST REROUTE
Fast reroute is a term used to describe two mechanisms whereby alternate paths are presignalled so that, should a path become unviable, traffic can be transferred onto a new path with minimal delay. The two mechanisms actually protect against different types of failure and can be characterized as either link protection or node protection.
As the name suggests, link protection protects against the failure of a single link by creating a bypass LSP between the two adjacent LSRs either side of the failed link (see Figure 7.3). In the event of a failure, all the affected LSPs are tunnelled through the bypass LSP using label stacking. This relies upon the use of labels, which are unique within the entire chassis (rather than unique on the interface). One major benefit of this is the fact that the labels for the inner LSP remain unchanged. This minimizes the signalling and computational requirements to achieve this form of bypass. In a large network with many nodes this reduction in signalling overhead can be significant.
Unfortunately, link protection is of no value if an LSR totally fails. On the failure of the LSR, all links from that LSR would go down. The LSR at the ingress to each failed link would identify the failure and attempt to tunnel the failed LSPs through an alternate path to the failed LSR (the next hop). Since that LSR is down, the ‘tunnel’ LSR would also be down and so fast reroute would fail. At this point, all the affected LSPs would be torn down and resignalled end to end. In a large network, the failure of a crucial LSR could cause a massive burst of signalling and path computation.
Node protection protects against the failure of an entire LSR or multiple links associated with a single LSR by creating a bypass LSP between the two LSRs adjacent to the failed LSR (see Figure 7.4). This requires a pre-signalled, alternate LSP for each affected LSP and, upon the detection of the failure, all the outbound packets will have a different label than they would have had. This is much more flexible in the sense that it is possible to route around multiple adjacent failures. However, the signalling and computational overhead of this mechanism are significantly greater than that for link protection as described above.
Bypass LSP
M5 |
M5 |
PE |
M5 |
X |
M5 |
PE |
|
Protected LSP
Figure 7.3 MPLS fast reroute, link protection

104 |
MULTIPROTOCOL LABEL SWITCHING (MPLS) |
Bypass LSP
M5 |
M5 |
PE |
M5 |
X |
M5 |
PE |
|
Protected LSP
Figure 7.4 MPLS fast reroute, node protection
In addition to the extra bypass path to avoid a failed node, node protection also creates a bypass LSP to avoid a failed single node. In large networks, this can require enormous amounts of state. However, in comparison to link protection, the impact of the failure of nodes protected by node protection will cause minimal signalling and computational overhead.
In general, the functional benefits of node protection outweigh the disadvantages associated with the extra state required. In the end, you have to decide whether the failure of an entire node is sufficiently likely to make the disadvantages of link protection under those circumstances more significant than the benefits of vastly reduced state associated with link protection.
The choice of protection mode will depend upon what has been implemented by your chosen vendors. Cisco and Juniper have both implemented both mechanisms. However, if you have other vendors’ equipment in your network, it is important to check their capabilities.
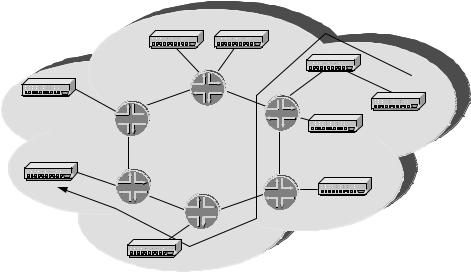
7.7 INTEGRATING ATM AND IP NETWORKS
Since both ATM switches and IP routers can be LSRs, MPLS provides the basis on which this integration can occur. It is generally held to be a good thing that IP networks and ATM networks be integrated with a single control plane and data plane. The main benefits are evident to operators with existing separate ATM and IP networks who wish to operate all the services on a single converged network. By using MPLS, a network provider can significantly reduce the impact of the migration. Equally importantly, it can change the period over which the migration is paid for. For businesses today, this can be an important issue. If new equipment can be purchased over a longer period, then this can make a significant difference to the profitability of the network in the earlier stages of deployment.
ATM switches utilize the VPI/VCI field to carry the label information and use their standard signalling mechanisms for exchanging label information. ATM LSRs also have support LDP as a label distribution protocol. This is the basis on which an LSP can be
7.8 GENERALIZED MPLS (GMPLS) |
105 |
3.220
101456
.120 1
101234
101345
0.202
Figure 7.5 Integrating MPLS and ATM networks
built end to end crossing both ATM and IP networks (see Figure 7.5). In so doing, a single ‘transport’ is created, which is independent of the underlying media.
7.8GENERALIZED MPLS (GMPLS)
Generalized MPLS takes the concept of MPLS and applies it to various types of Layer 1, Layer 2 or Layer 3 networks. GMPLS devices can have interfaces of the following types:
•fibre-switched capable (FSC);
•lambda-switched capable (LSC);
•time-division-multiplexing switched capable (TSC);
•packet-switched capable (PSC).
Within the GMPLS framework, LSPs must start and finish on links of the same capability. However, the LSP can transit any type of link within the network.
The implication of these extensions is that LSPs can now be built across a network and that devices at Layer 1, Layer 2 and Layer 3 can all participate in the decision how to route the LSPs. Thus, Optical Cross Connects (OXC) and SONET/SDH Add-Drop Multiplexers (ADM) in the core of operators’ transport networks can take part in the establishment of LSPs (see Figure 7.6).

106 |
MULTIPROTOCOL LABEL SWITCHING (MPLS) |
|
ADM |
ADM |
ADM |
|
ADM |
ADM |
|
|
|
ADM |
Figure 7.6 Integrating MPLS and Optical switches with GMPLS
GMPLS differs from traditional MPLS in the following ways:
•GMPLS requires a separate Data Control Network over which control messages can be sent. RSVP-TE is an IP-based protocol so cannot be carried natively over the data plane (as is the case with traditional MPLS).
•RSVP-TE has been further extended to allow the LSR to request labels of the form applicable to the particular link (e.g. a wavelength, a fiber, or a time-slot).
•GMPLS can create bi-directional LSPs. Unlike traditional MPLS, in which LSPs are strictly unidirectional, non-packet LSPs in GMPLS can be signalled to be capable of carrying data in both directions over a single path.
GMPLS requires that RSVP-TE and the Link Management Protocol (LMP) for the particular type of link interact very closely. When establishing an LSP, the following steps are required.
1.The LMP informs RSVP-TE of the following elements:
(a)the Traffic Engineering Link (an interface or sub-interface based on time-slot, wavelength, etc.);
(b)resources available on the TE Link;
(c)the control peer.
7.8 GENERALIZED MPLS (GMPLS) |
107 |
2.GMPLS derives the specific attributes of the new LSP from the configuration of the node. It requests that RSVP-TE signal one or more specific paths described by the TE Link addresses.
3.RSVP-TE determines the adjacent TE Link, the associated control adjacency and control channel, and the transmission parameters (e.g. IP address). It requests that the LMP allocate the required resources from the TE Link. If the LMP is able to allocate the required resource, then a label is allocated. RSVP-TE then sends a PathResv message towards the destination router.
4.When the PathResv message reaches the destination router, the LMP tries to allocate the requested resources. If it is successful, then RSVP-TE transmits a ResvMsg back towards the source router.
5.Once the ResvMsg reaches the source router, the LSP is established.
As with traditional MPLS, a link state protocol is used to carry the traffic engineering information throughout the network. GMPLS uses OSPF-TE with added extensions to populate the TED, in addition to those used in traditional MPLS networks. The new information is carried in a TLV called the interface switching capability descriptor. The new TLV contains the following attributes:
•signal type (minimum LSP bandwidth);
•encoding type;
•switching type.
GMPLS runs the constrained shortest path first (CSPF) process in exactly the same way as traditional MPLS. The only difference is that it takes the additional constraints into account when calculating the constrained path.
The output of the CSPF algorithm must be a strict path. GMPLS is incapable of using a loose path.
