
- •Table of Contents
- •Cisco Network Security Little Black Book
- •Introduction
- •Is this Book for You?
- •How to Use this Book
- •The Little Black Book Philosophy
- •Chapter 1: Securing the Infrastructure
- •In Brief
- •Enterprise Security Problems
- •Types of Threats
- •Enterprise Security Challenges
- •Enterprise Security Policy
- •Securing the Enterprise
- •Immediate Solutions
- •Configuring Console Security
- •Configuring Telnet Security
- •Configuring Enable Mode Security
- •Disabling Password Recovery
- •Configuring Privilege Levels for Users
- •Configuring Password Encryption
- •Configuring Banner Messages
- •Configuring SNMP Security
- •Configuring RIP Authentication
- •Configuring EIGRP Authentication
- •Configuring OSPF Authentication
- •Configuring Route Filters
- •Suppressing Route Advertisements
- •Chapter 2: AAA Security Technologies
- •In Brief
- •Access Control Security
- •Cisco Secure Access Control Server
- •Immediate Solutions
- •Configuring TACACS+ Globally
- •Configuring TACACS+ Individually
- •Configuring RADIUS Globally
- •Configuring RADIUS Individually
- •Configuring Authentication
- •Configuring Authorization
- •Configuring Accounting
- •Installing and Configuring Cisco Secure NT
- •Chapter 3: Perimeter Router Security
- •In Brief
- •Defining Networks
- •Cisco Express Forwarding
- •Unicast Reverse Path Forwarding
- •TCP Intercept
- •Network Address Translation
- •Committed Access Rate
- •Logging
- •Immediate Solutions
- •Configuring Cisco Express Forwarding
- •Configuring Unicast Reverse Path Forwarding
- •Configuring TCP Intercept
- •Configuring Network Address Translation (NAT)
- •Configuring Committed Access Rate (CAR)
- •Configuring Logging
- •Chapter 4: IOS Firewall Feature Set
- •In Brief
- •Port Application Mapping
- •IOS Firewall Intrusion Detection
- •Immediate Solutions
- •Configuring Port Application Mapping
- •Configuring IOS Firewall Intrusion Detection
- •Chapter 5: Cisco Encryption Technology
- •In Brief
- •Cryptography
- •Benefits of Encryption
- •Symmetric and Asymmetric Key Encryption
- •Digital Signature Standard
- •Cisco Encryption Technology Overview
- •Immediate Solutions
- •Configuring Cisco Encryption Technology
- •Chapter 6: Internet Protocol Security
- •In Brief
- •IPSec Packet Types
- •IPSec Modes of Operation
- •Key Management
- •Encryption
- •IPSec Implementations
- •Immediate Solutions
- •Configuring IPSec Using Manual Keys
- •Configuring Tunnel EndPoint Discovery
- •Chapter 7: Additional Access List Features
- •In Brief
- •Wildcard Masks
- •Standard Access Lists
- •Extended Access Lists
- •Reflexive Access Lists
- •Dynamic Access Lists
- •Additional Access List Features
- •Immediate Solutions
- •Configuring Standard IP Access Lists
- •Configuring Extended IP Access Lists
- •Configuring Extended TCP Access Lists
- •Configuring Named Access Lists
- •Configuring Commented Access Lists
- •Configuring Dynamic Access Lists
- •Configuring Reflexive Access Lists
- •Appendix A: IOS Firewall IDS Signature List
- •Appendix B: Securing Ethernet Switches
- •Configuring Management Access
- •Configuring Port Security
- •Configuring Permit Lists
- •Configuring AAA Support
- •List of Figures
- •List of Tables
- •List of Listings

Chapter 5: Cisco Encryption Technology
In Brief
Many organizations are wary about transmitting sensitive data over networks. Hospitals transmit sensitive patient information to insurance companies. Banks and stock exchange companies transfer vital financial information over networks. There is a valid fear that the data could be viewed, altered in transit, or used by malicious people to harm patients, cause lawsuits, or defraud corporations. People want this kind of data communication to remain private. Almost every company has transactions that need to be protected from eavesdroppers. Companies want to ensure that when sensitive data passes over a medium susceptible to eavesdropping, it cannot be altered or observed. Data encryption is designed to protect sensitive data.
Cisco's implementation of Network−layer encryption allows security administrators to smoothly integrate the security of encryption into a network. The integration is transparent to end users and their applications. Encryption must happen only at the edge of the network on the LAN where the sensitive data originates, and decryption is not necessary until the data reaches the router on the far LAN where the destination host resides. Network managers retain the option of encrypting anywhere in the data path. By encrypting after the User Datagram Protocol (UDP) or TCP headers, so that only the IP pay−load is encrypted, Cisco IOS network−layer encryption allows all intermediate routers and switches to forward the traffic as they would any other IP packets. This payload−only encryption allows flow switching and all access list features to work with the encrypted traffic, just as they would with plain text traffic, thereby preserving desired Quality of Service (QoS) for all data. Users can send encrypted data over the Internet transparently.
This chapter examines Cisco's proprietary encryption solution known as Cisco Encryption Technology. I will present introductions to many of the components that are used to provide encryption services for Cisco Encryption Technology, as well as services for IPSec, which will be discussed in the next chapter. In this chapter, I will explain what encryption is, its history, how it works, and the security issues it solves. Symmetric and asymmetric keys will be discussed, and the Diffie−Hellman key algorithm and message−digest will be explained in detail. Finally, the Cisco proprietary encryption solution will be discussed, and I will present the methods that are used to configure it.
Cryptography
Cryptography, also known as encryption, is a method of transforming original data, called plaintext or cleartext, into a form that appears to be random and unreadable, which is called ciphertext. A simpler definition would be that cryptography is the method of storing and transmitting data in a form that only the intended recipient can read or process. Cryptography is the science of secure and secret communications. Security allows the sender to transform information into a coded message by using a secret key, a piece of information known only to the sender and the authorized receiver. The authorized receiver can decode the cipher to recover hidden information. If unauthorized individuals somehow receive the coded message, they should be unable to decode it without knowledge of the key. The key, which is usually a variable−length series of bits, works with the encryption algorithm to encrypt or decrypt messages. The algorithm, the set of mathematical rules, dictates how enciphering and deciphering take place. Many algorithms are publicly known and are not the secret part of the encryption process.
The way that encryption algorithms work can be kept secret from the public, but many of them are publicly known and well understood. If the internal mechanisms of the algorithm are not a secret,
156
then something must be. The secret behind the use of a well−known encryption algorithm is the key. The key can be any value made up of a large sequence of random bits. Is it just any random number of bits crammed together? Not really. An algorithm contains a keyspace, which is a range of values that can be used to construct a key. The key is made up of random values within the keyspace range. The larger the keyspace, the more available values can be used to represent different keys, and the more random the keys are, the harder it is for intruders to figure them out. A large keyspace allows for more possible keys. The encryption algorithm should use the entire keyspace and choose the values to make up the keys as randomly as possible. If a smaller keyspace were used, there would be fewer values to choose from when forming a key. This would increase an attacker's chance of figuring out the key value and deciphering the protected information.
After a message is transformed into ciphertext, neither human nor machine should be able to properly process it until it is decrypted. This enables the transmission of confidential information over insecure channels without unauthorized disclosure. When data is stored on a computer, it is usually protected by logical and physical access controls. When this same sensitive information is sent over a network, you can no longer take these controls for granted, and the information is in a much more vulnerable state. If an eavesdropper captures a message as it passes between two people, the eavesdropper will be able to view the message, but it appears in its encrypted form and is therefore unusable. Even if the eavesdropper knows the algorithm that the two people are using to encrypt and decrypt the information, without the key, the information remains useless to the eavesdropper.
Modern day cryptography is a science that has one goal: to protect sensitive information by encoding it in a format that is unreadable. However, most modern cryptographic algorithms can be broken and the information can be revealed if the attacker is given enough time and resources to find the key.
History of Cryptography
Cryptography dates back as early as 4000 B.C. when hieroglyphics were used by the Egyptians to decorate tombs to tell the story of the life of the deceased person. This practice was not as much to hide the messages as it was to make them more majestic and ceremonial. Encryption methods began to evolve from ceremonial to more practical applications for war, crisis, and espionage. Throughout history, individuals and governments alike have worked to protect communication between trusted sources through the use of encryption. The first known use of encryption by a government for military purposes was around 400 B.C. It was used by the Spartans in the form of a thin strip of papyrus wrapped around a staff. Messages were written down or up the length of the staff and then the papyrus was unwrapped. For the message to be read, the papyrus had to be wrapped around a staff equal in diameter to the first staff. This system is called a skytale cipher, and it was used to send secret messages between Greek warriors. Without a staff of equal diameter (d) and minimum length (1), it would be difficult to decode the message because the message would appear to be random characters written on the unwrapped papyrus. The keys you need to decipher the skytale cipher are d and l. Figure 5.1 displays an example of the Scytale cipher, and the following versions of the alphabet demonstrate the technique. First you see the wrapped version:
ADGJMPSVY
BEHKNQTWZ
CFILORUX
157
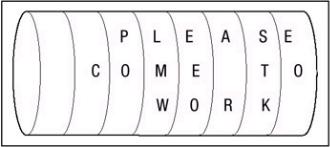
Figure 5.1: An Example of the Scytale cipher.
Then you see the unwrapped version:
ADGJMPSVYBEHKNQTWZCFILORUX
At or around 50 B.C., Julius Caesar used a system of cryptography known as the Caesar Cipher, or C3. It shifted each letter three places forward in the alphabet (for example, "A" shifts to "D," "K" shifts to "N," etc.). In the following example, the first row is plaintext and the second row is the equivalent ciphertext. The distance of the letter placement within the algorithm is not important to the scheme, and in fact, neither is the order of the letters that are chosen. Because only one alphabet is used with this sort of cipher, the Caesar Cipher is referred to as a monoalphabetic substitution cipher, wherein each letter is mapped into another letter in a one−to−one fashion.
ABCDEFGHIJKLMNOPQRSTUVWXYZ−Plaintext
DEFGHIJKLMNOPQRSTUVWXYZABC−Ciphertext
During the Middle Ages, cryptography started to progress. All of the governments of western Europe used cryptography in one form or another, and codes started to become more popular. Ciphers were commonly used to keep in touch with ambassadors. The first major advances in cryptography were made in Italy. In the middle of the 1400s, an elaborate organization was created in Venice with the sole purpose of dealing with cryptography. There were three cipher secretaries who solved and created ciphers used by the government.
Around the same time Leon Battista Alberti developed the polyalphabetic substitution. A polyalphabetic substitution is a technique in which different ciphertext symbols can represent the same plaintext symbol. This makes it more difficult to use frequency analysis to interpret ciphertext. To develop this technique, Alberti analyzed all of the available methods used for breaking ciphers and devised a cipher he hoped would render these techniques invalid. What he designed were two copper disks that fit into each other, and each had an alphabet inscribed upon it. To start the enciphering, a predetermined letter on the inner disk is lined up with any letter on the outer disk, which is written as the first character of the ciphertext. The disks are kept stationary, with each plaintext letter on the inner disk aligned with a ciphertext letter on the outer disk. After a few words of ciphertext, the disks are rotated so that the index letter on the inner disk is aligned with a new letter on the outer disk, and in this manner, the message is enciphered. Because the disk was rotated every few words, this allowed the cipher to change enough to limit the effectiveness of frequency analysis. This technique is very weak; however, it was the ingenious idea of rotating the disks, which therefore changed the cipher many times within a message, that became a major breakthrough in cryptography.
Thomas Jefferson, around 1795, invented the wheel cipher. Although he never did much with it. The wheel cipher consists of a set of 26 wheels, each with the letters of the alphabet in random order. The key to the system is the order in which the wheels where placed on an axle. The message is encoded by aligning the letters along the rotational axis of the axle such that the desired message is formed. Any other row of aligned letters can then be used as the ciphertext for transmission. The decryption requires the recipient to align the letters of the ciphertext along the rotational axis and
158
find a set of aligned letters that makes linguistic sense as plaintext. This is the message. There is a small probability that there will be two sensible messages from the decryption process, but this can be checked easily by the originator.
In 1844, the development of cryptography was dramatically altered by the invention of the telegraph. Communication with the telegraph was by no means secure, so ciphers were needed to transmit secret information. The public's interest in cryptography blossomed, and many individuals attempted to formulate their own cipher systems. The advent of the telegraph provided the first instance in which a base commander could be in instant communication with his field commanders during battle. Thus, a field cipher was needed. At first, the military used a Vigenere cipher with a short repeating keyword, but in 1863, a solution was discovered by Friedrich W. Kasiski for all periodic polyalphabetic ciphers, which until this time were considered unbreakable, so the military had to search for a new cipher to replace the Vigenere.
In the 1920s, Herbert Yardley, known as the "Father of American Cryptography," was in charge of the top−secret U.S. MI−8 organization. This organization has come to be known as the Black Chamber. MI−8 cracked the codes of a number of different countries. In 1929, the U.S. State Department, acting upon the orders of then President Herbert Hoover, closed MI−8, much to the disagreement of Yardley.
To feed his family, Yardley, hard−pressed to find work during the depression, wrote a book describing the secret workings of MI−8. It was called The American Black Chamber and became a best seller. Many people criticized him for divulging secrets and glorifying his own actions during the war.
Up to 1917, transmissions sent over telegraph wires were encoded in Baudot code for use with teletypes. The American Telephone and Telegraph company was very concerned about how easily the teletypes could be read, so Gilbert S. Vernam developed a system that added together the plaintext electronic pulses with a key to produce ciphertext pulses. It was difficult to use at times because keys were cumbersome. Vernam developed a machine to encipher messages, but the system was never widely used.
The use of cryptographic machines dramatically changed the nature of cryptography and cryptanalysis. Cryptography became intimately related to machine design, and security personnel became involved with the protection of these machines. The basic systems remained the same, but the method of encryption became reliable and electromechanical.
As computers came to be, the possibilities for encryption methods and devices advanced, and cryptography efforts expanded exponentially. This era brought unprecedented opportunity for cryptographic designers and encryption techniques. The most well−known and successful project was Lucifer, which was developed at IBM. Lucifer introduced complex mathematical equations and functions that were later adopted and modified by the U.S. National Security Agency (NSA) to come up with the U.S. Data Encryption Standard (DES). DES has been adopted as a federal government standard, is used worldwide for financial transactions, and is imbedded into numerous commercial applications. DES has had a rich history in computer−oriented encryption and has been in use for more than 20 years.
A majority of the protocols developed at the dawn of the computing age have been upgraded to include cryptography to add the necessary layers of protection. Encryption is used in hardware devices and software to protect data, banking transactions, corporate extranets, email, Web transactions, wireless communication, storing of confidential information, faxes, and phone calls.
159
