
Microsoft Windows XP Networking Inside Out
.pdf
5 Chapter
Part 2: Internet Networking
The most common example concerns a private local area network (LAN) and the public Internet. A firewall can be used between the two so that users on the private network can access the Internet, but Internet users cannot access the private network. In the following schematic illustration, the LAN can reach across the firewall to draw upon the Internet, but activity originating from the Internet cannot cross over the firewall and compromise the LAN’s security.
Network Protected by a Firewall
|
Internet |
LAN |
Firewall |
Firewalls can also be configured to prevent LAN users from accessing the Internet or to restrict TCP/IP traffic so that only certain ports can transmit across the firewall.
Firewall solutions can be in the form of either hardware or software. Each has its own advantages and disadvantages, and staunch firewall enthusiasts might argue for one or the other. However, from a networking person’s point of view, both hardware and software solutions can be very effective ways to protect your network. ICF is a softwarebased firewall solution.
For more information on firewalls and their use, as well as best practices related to ICF and other firewall products, be sure to read Chapter 20, “Maintaining Network Security.”
Understanding Internet Connection Firewall
ICF is readily available in Windows XP and works with any network connection. Before getting into the specifics of ICF configuration, it is important to understand how ICF works, the features it provides, and how it can be used in a home or small office network. It is important to note that ICF was specifically developed to protect modem and broadband Internet connections—it was not designed for workstations residing on
118
2: Internet Networking

Chapter 5: Using Internet Connection Firewall
large networks where other types of Internet access are used. In those networks, either firewall hardware or software on Windows 2000 servers is used to control and manage Internet access. ICF, however, was designed to support either a stand-alone computer (that is, one not providing a shared connection to other systems) or a computer that is providing a shared Internet connection to other computers on a small network.
For more information about using a Windows XP computer to share an Internet connection with multiple computers, see “Using Internet Connection Sharing,” page 301.
How ICF Works
ICF works with an Internet connection to provide security from external attacks. ICF uses a method of protection known as the table method, in which a table or list of outbound and inbound IP addresses is maintained. Consider first how ICF works when a standalone computer uses ICF. You enable ICF on the Internet connection, as detailed in “Activating and Configuring ICF” on page 124. Using your Web browser, you request a Web page. ICF makes an entry in its outbound connections table noting the IP address
of the site you are requesting. When the Web page is served back to the computer, ICF examines the IP packets and looks at the IP addresses. If ICF finds a match for the sending address in the list of destination addresses for outbound traffic, the assumption is that you requested the IP traffic and therefore ICF allows the traffic to enter the computer. However, if any traffic arrives at the firewall that does not match a destination IP address listed in the table, the IP packets are dropped and are not processed by the computer.
ICF is considered a stateful firewall because it examines all traffic passing in and out of the firewall and makes decisions concerning that traffic as needed. In other words, ICF considers the current state of the packets and determines whether they are allowed or not based on the ICF table, as the following diagram shows.
How ICF Works
1. Computer requests www.msn.com.
2. Internet returns www.msn.com.
Internet
3. ICF accepts www.msn.com.
4. ICF rejects all unsolicited traffic.
Internet
Connection
Firewall
119
Chapter 5
2: Internet Networking

5 Chapter
120
Part 2: Internet Networking
You can also protect an entire network by enabling ICF on the computer that directly accesses the Internet and by using Internet Connection Sharing (ICS) on the LAN. In the case of a network using ICS, the computer hosting the Internet over an ICF-enabled connection also serves as the ICS host for the rest of the LAN. All other computers on the network access the ICS host computer to connect to the Internet, so all network requests are recorded and managed in the ICF table, as shown in this illustration.
Software-based Firewall, ICS Network
ICS clients |
|
|
|
ICS host |
Internet |
|
|
|
|
Hub |
|
|
Internet |
|
LAN |
Connection |
|
|
Firewall |
|
Because all inbound traffic is dropped unless it has been specifically requested from an internal network client, ICF blocks some types of traffic that can be potentially dangerous, but might also be wanted on your network. For example, all incoming ICMP traffic (such as ping requests) is blocked as well as all Remote Desktop traffic originating from outside the LAN. Because you might want to allow ICMP or Remote Desktop traffic, ICF provides a way to override the table configuration for certain services, which you can learn more about in “Enabling Services” on page 130.
Understanding ICF and Protocols
ICF works on a table basis, not on a protocol-by-protocol basis. Although some firewalls allow you to block certain protocols, ICF is concerned with keeping traffic that is not explicitly requested from entering the local computer or network. For this reason, ICF does not place any restrictions on protocols. If you want to download
2: Internet Networking

Chapter 5: Using Internet Connection Firewall
music or movies, you won’t have any problems with ICF because there will be a table entry for your request and the data will be allowed to pass. However, if you want to play games over the Internet where an Internet client contacts your computer, ICF will not allow that traffic because the traffic originated from outside your LAN (as an invitation to play the game) and thus won’t have a table entry in ICF. As you work with ICF, keep in mind that ICF allows any traffic that arrives from a request you made regardless of its protocol and likewise blocks all unsolicited traffic originating from outside the network despite its protocol.
How to Use ICF
ICF is easy to configure and use as long as you remember two simple rules:
●All Internet connections should be firewalled. For example, if your computer has a broadband connection to the Internet as well as a dial-up connection to the Internet, both the broadband connection and the dial-up connection should be firewalled for complete protection. Failure to turn on ICF for one of the Internet connections is considered a security breach because your computer or network will not be protected whenever that connection is used.
●Internal network connections should usually not be firewalled. Network interface cards (NICs) used to communicate on your local network must not be firewalled. If they are, computers on the network will not be able to access your computer because the ICF table will not allow any network traffic to enter the computer that is not explicitly requested by you. ICF is used on the Internet connection only, not on the internal network connections.
When You Should Use ICF
Considering the two usage rules in the previous section, a few different scenarios describing when ICF should be used and how it should be used are provided in the following sections.
Accessing the Internet from a Single Computer
If you are using a single computer, enable ICF on your Internet connection. If you have multiple Internet connections, enable ICF on each connection so that you are always protected, no matter which connection you might be using at the moment. Remember that ICF works with individual connections in Network Connections, not on your computer as a whole. When multiple Internet connections are used, you must firewall each connection for complete protection.
Chapter 5
121
2: Internet Networking
5 Chapter
122
Part 2: Internet Networking
Accessing the Internet from a Network Using ICS
If you are using ICS (see “Using Internet Connection Sharing,” page 301, to learn more about ICS), you should enable ICF on the Internet connection residing on the ICS host computer. If you have multiple Internet connections on the ICS host computer, enable ICF on each Internet connection. However, do not enable ICF on the local area connections between the ICS host and ICS clients. If you firewall other internal network connections, you will have network connectivity problems between computers.
Accessing the Internet from a
Network with Multiple Internet Connections
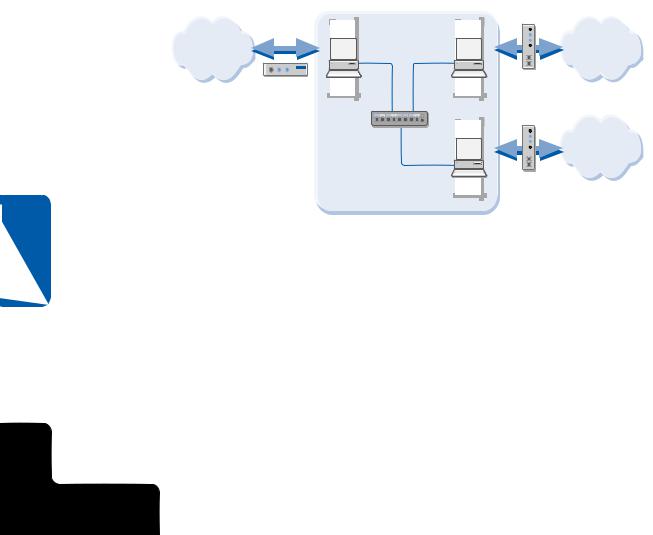
If you are using a network in which several computers directly access the Internet through broadband or dial-up connections, you need to use ICF on each connection to the Internet, as shown in the following illustration. Again, make sure you do not firewall NICs that internally connect the LAN—only enable ICF on the external Internet connections.
ICF Enabled on Multiple Internet Connections
Internet |
|
Dial-up |
|
modem |
ICF |
|
Hub
LAN
|
Internet |
|
DSL |
ICF |
modem |
|
|
|
Internet |
|
DSL |
ICF |
modem |
|
Accessing the Internet from a Large Network with Poor Security
Some large LAN and WAN environments do not have firewalls or any other kind of protective measures between them and their Internet connection. Although this situation is becoming less and less common, many colleges, universities, and other institutions continue to maintain an open network policy.
In such situations, workstations normally use the same connection to access both LAN/ WAN and Internet resources, so it’s normally wise to use some sort of firewall to protect your workstation. However, remember that although ICF will protect your Internet connection, it can cause headaches if you need to perform file and printer sharing with other Windows clients and servers within the LAN or WAN. This topic
is discussed in “Enabling File and Printer Sharing with ICF,” page 132.
2: Internet Networking

Chapter 5: Using Internet Connection Firewall
When You Should Not Use ICF
As a general rule, ICF can be used in most situations when you want to protect your computer from Internet attacks. However, you should not use ICF if
●You are using another firewall. If you are using a residential gateway or another firewall software product, do not use ICF. You should only use one firewall product, whether that product is a hardware or software solution. Multiple firewall products usually do not work together and can cause you to lose your Internet connection. So, make a choice, but do not use ICF when another firewall solution is used.
●You are using a mail client that requires remote procedure calls. Some mail programs, such as Microsoft Outlook in a Microsoft Exchange server environment, use remote procedure calls (RPCs), which allow mail servers to contact the program when there is mail to be delivered. ICF will block this kind of traffic because it has not been requested internally, so in some cases, ICF will simply not allow you to receive your mail automatically. Instead, you have to manually check for mail. If you are using Microsoft Outlook as a way to connect to an ISP mail server, Outlook will work fine with ICS. See “Using ICF with E-mail Services,” page 134, for more information.
●You need to share files across a virtual private network (VPN) connection, because ICF can block such sharing. However, a workaround for this problem is presented in “Enabling File and Printer Sharing with ICF,” page 132.
What ICF Does Not Do
ICF is a basic firewall product that blocks traffic; however, it does not meet every possible need, and it does not protect you from every possible threat. For example:
●ICF does not protect you from viruses or worms. Downloaded viruses, e-mail viruses, and worms are not detected by ICF. You need to use antivirus software with ICF for complete protection against these dangers.
●ICF does not protect you from Trojan horse programs. Once they get into your computer (usually in e-mail you receive), Trojan horse programs gather information from your computer, such as addresses from an e-mail address book, and send themselves in e-mail addressed to your contacts, spreading themselves further. Because ICF is only concerned with inbound traffic, ICF does not inspect outbound traffic for these threats. To ensure that your computer is not running Trojan horse programs, you need a program that can safeguard your computer. Some third-party firewall products,
Chapter 5
123
2: Internet Networking

5 Chapter
124
Part 2: Internet Networking
such as ZoneAlarm (www.zonealarm.com) provide this kind of protection, but you should always use a combination of firewall and antivirus software for complete protection.
●If your computer is using ICS to share its connection to the Internet with the other computers on your network, ICF does not protect your computer from internal attacks and threats. ICF only protects your Internet connection. If an internal user on your network decides to attack other computers inside the network or runs a Trojan horse application that attempts to do the same thing, ICF provides no protection for this kind of attack.
Internal and external network threats, as well as countermeasures for them, are covered in Chapter 20, “Maintaining Network Security.”
Activating and Configuring ICF
ICF is easy to enable and generally easy to configure, depending on your needs. There are several important actions that you need to know about, and in this section, you can explore how to best configure and use ICF.
note You must be logged on with an account that has administrative privileges to enable and configure ICF.
Enabling ICF
You can enable ICF quickly and easily using a single check box. Follow these steps:
1Open Network Connections. From the Windows XP Start menu, choose Connect To, Show All Connections; from the Classic Start menu, choose Settings, Network Connections.
2In the Network Connections window, right-click the Internet connection on which you want to enable ICF and choose Properties.
3In the Properties dialog box, select the Advanced tab, which is shown in Figure 5-1.
4In the Internet Connection Firewall section, select the Protect My Computer And Network check box and click OK. The connection is now firewalled.
5If you are using additional Internet connections, repeat steps 1–4 to enable ICF on those connections as well.
2: Internet Networking

Chapter 5: Using Internet Connection Firewall
Figure 5-1. Select the check box in the Internet Connection Firewall section to enable ICF.
note If your computer does not have a NIC, you’ll not see the Internet Connection Sharing section that appears in Figure 5-1.
caution If you open the Properties dialog box for your LAN connection, you’ll also see that ICF is available on the Advanced tab. This is due to the fact that the Properties dialog boxes are the same for all network connections. However, this does not mean that ICF should be enabled on any NICs that are not directly connected to the Internet. If you are using ICS to share your Internet connection with an internal network, you should only enable ICF on the connections that directly connect to the Internet; all other internal connections should not be firewalled.
Using the ICF Log
When you enable ICF for an Internet connection, the firewall becomes active and immediately starts working. ICF gives you the option of logging the events that occur with ICF, but the log is not activated or configured by default. Using ICF’s simple log file, you can log dropped packets as well as all successful connections.
If you choose to log dropped packets, you can view the log file and see what attempts to access your computer over the Internet have been thwarted. This gives you clues about anyone who might be trying to tamper with your network or PC. If you log successful
Chapter 5
125
2: Internet Networking

Part 2: Internet Networking
connections, you’ll see the destination IP address of every site that you have visited. But this will cause the log file to grow rapidly, especially if the Internet is used a lot on the local computer or on an ICS network. You do, however, have the ability to determine the maximum size to which individual log files can grow. To configure the security log, follow these steps:
1Open Network Connections.
2Right-click an Internet connection on which ICF is enabled and choose Properties.
3In the Properties dialog box, select the Advanced tab. Click the Settings button.
4Select the Security Logging tab shown in Figure 5-2.
5Under Logging Options, select either or both Log Dropped Packets and Log Successful Connections.
6By default, the log file is named pfirewall.log, and it is stored in your Windows directory. If you want to store it elsewhere, click the Browse button or type another destination in the Name box.
7The default maximum log file size is 4096 KB. You can decrease this value if you like or increase it to a maximum size of 32,767 KB.
8Click OK when you’re done.
5 Chapter
Figure 5-2. Select the logging options and configuration you want for
ICF-protected connections.
126
2: Internet Networking
Chapter 5: Using Internet Connection Firewall
note When the log file reaches its maximum size, as configured on the Security Logging tab, the information is written to a file named pfirewall.log.1, and the newest data is saved in pfirewall.log. Also note that log file settings are global; they apply to all firewalled connections on the computer.
Viewing the Log File
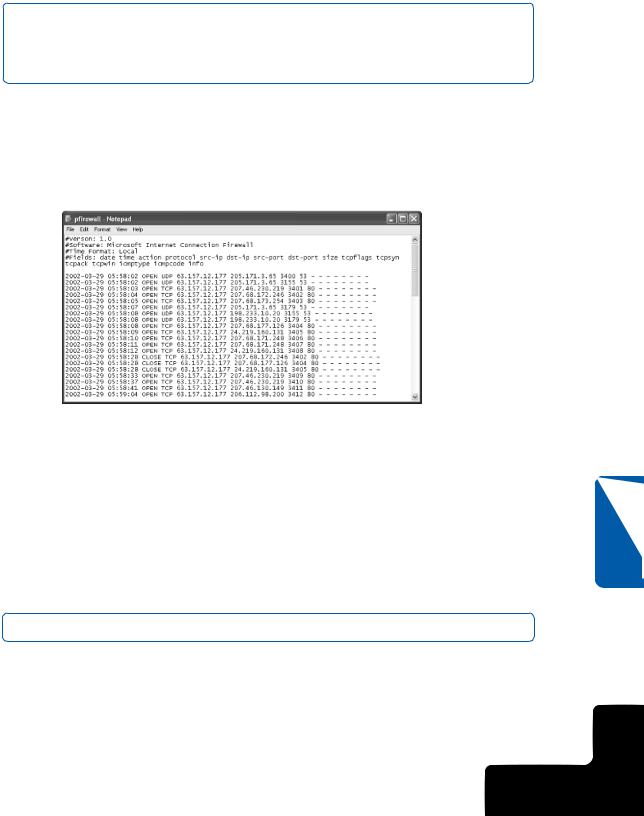
Once logging is turned on, you can view the log file at any time by opening it with Notepad, any text editor, or any word processing application. Figure 5-3 shows that the log file contains IP information about the connections that you have decided to log. In this example, both successful connections as well as dropped packets are being logged.
Figure 5-3. The ICF log file contains IP addressing information for the data you chose to log.
Understanding the Log File
The ICF log file contains IP information about the connection or dropped packets. Figure 5-3 shows that the fields that are logged are listed in the order by which they are logged. The data below the field listing corresponds directly to the fields, although field data does not line up with the headers in Notepad. The ICF log is
a W3C Extended File format log, which can also be opened and analyzed (or even written to a database) by third-party logging utilities. Table 5-1 on the next page describes each of the logging fields.
For more information on how to best utilize W3C Extended File logs, see “Examining Log Files,” page 582.
Chapter 5
127
2: Internet Networking
