
- •Contents
- •Foreword to the First Edition
- •Preface to the Third Edition
- •Preface to the Second Edition
- •Preface to the First Edition
- •1 SIP and the Internet
- •1.1 Signaling Protocols
- •1.2 Internet Multimedia Protocol Stack
- •1.2.1 Physical Layer
- •1.2.2 Data/Link Layer
- •1.2.3 Network Layer
- •1.2.4 Transport Layer
- •1.2.5 Application Layer
- •1.2.6 Utility Applications
- •1.2.7 Multicast
- •1.3 Internet Names
- •1.4 URLs, URIs, and URNs
- •1.5 Domain Name Service
- •1.5.1 DNS Resource Records
- •1.5.2 Address Resource Records (A or AAAA)
- •1.5.3 Service Resource Records (SRV)
- •1.5.4 Naming Authority Pointer Resource Records (NAPTR)
- •1.5.5 DNS Resolvers
- •1.6 Global Open Standards
- •1.7 Internet Standards Process
- •1.8 A Brief History of SIP
- •1.9 Conclusion
- •References
- •2 Introduction to SIP
- •2.1 A Simple Session Establishment Example
- •2.2 SIP Call with a Proxy Server
- •2.3 SIP Registration Example
- •2.4 SIP Presence and Instant Message Example
- •2.5 Message Transport
- •2.5.1 UDP Transport
- •2.5.2 TCP Transport
- •2.5.3 TLS Transport
- •2.5.4 SCTP Transport
- •2.6 Transport Protocol Selection
- •2.7 Conclusion
- •2.8 Questions
- •References
- •3 SIP Clients and Servers
- •3.1 SIP User Agents
- •3.2 Presence Agents
- •3.3 Back-to-Back User Agents
- •3.4 SIP Gateways
- •3.5 SIP Servers
- •3.5.1 Proxy Servers
- •3.5.2 Redirect Servers
- •3.5.3 Registrar Servers
- •3.6 Uniform Resource Indicators
- •3.7 Acknowledgment of Messages
- •3.8 Reliability
- •3.9 Multicast Support
- •3.10 Conclusion
- •3.11 Questions
- •References
- •4 SIP Request Messages
- •4.1 Methods
- •4.1.1 INVITE
- •4.1.2 REGISTER
- •4.1.5 CANCEL
- •4.1.6 OPTIONS
- •4.1.7 SUBSCRIBE
- •4.1.8 NOTIFY
- •4.1.9 PUBLISH
- •4.1.10 REFER
- •4.1.11 MESSAGE
- •4.1.12 INFO
- •4.1.13 PRACK
- •4.1.14 UPDATE
- •4.2 URI and URL Schemes Used by SIP
- •4.2.1 SIP and SIPS URIs
- •4.2.2 Telephone URLs
- •4.2.3 Presence and Instant Messaging URLs
- •4.3 Tags
- •4.4 Message Bodies
- •4.5 Conclusion
- •4.6 Questions
- •References
- •5 SIP Response Messages
- •5.1 Informational
- •5.1.1 100 Trying
- •5.1.2 180 Ringing
- •5.1.3 181 Call is Being Forwarded
- •5.1.4 182 Call Queued
- •5.1.5 183 Session Progress
- •5.2 Success
- •5.2.2 202 Accepted
- •5.3 Redirection
- •5.3.1 300 Multiple Choices
- •5.3.2 301 Moved Permanently
- •5.3.3 302 Moved Temporarily
- •5.3.4 305 Use Proxy
- •5.3.5 380 Alternative Service
- •5.4 Client Error
- •5.4.1 400 Bad Request
- •5.4.2 401 Unauthorized
- •5.4.3 402 Payment Required
- •5.4.4 403 Forbidden
- •5.4.5 404 Not Found
- •5.4.6 405 Method Not Allowed
- •5.4.7 406 Not Acceptable
- •5.4.8 407 Proxy Authentication Required
- •5.4.9 408 Request Timeout
- •5.4.11 410 Gone
- •5.4.12 411 Length Required
- •5.4.13 412 Conditional Request Failed
- •5.4.14 413 Request Entity Too Large
- •5.4.15 414 Request-URI Too Long
- •5.4.16 415 Unsupported Media Type
- •5.4.17 416 Unsupported URI Scheme
- •5.4.18 417 Unknown Resource Priority
- •5.4.19 420 Bad Extension
- •5.4.20 421 Extension Required
- •5.4.21 422 Session Timer Interval Too Small
- •5.4.22 423 Interval Too Brief
- •5.4.23 428 Use Identity Header
- •5.4.24 429 Provide Referror Identity
- •5.4.25 430 Flow Failed
- •5.4.26 433 Anonymity Disallowed
- •5.4.27 436 Bad Identity-Info Header
- •5.4.29 438 Invalid Identity Header
- •5.4.30 439 First Hop Lacks Outbound Support
- •5.4.31 440 Max-Breadth Exceeded
- •5.4.32 470 Consent Needed
- •5.4.33 480 Temporarily Unavailable
- •5.4.34 481 Dialog/Transaction Does Not Exist
- •5.4.35 482 Loop Detected
- •5.4.36 483 Too Many Hops
- •5.4.37 484 Address Incomplete
- •5.4.38 485 Ambiguous
- •5.4.39 486 Busy Here
- •5.4.40 487 Request Terminated
- •5.4.41 488 Not Acceptable Here
- •5.4.42 489 Bad Event
- •5.4.43 491 Request Pending
- •5.4.44 493 Request Undecipherable
- •5.4.45 494 Security Agreement Required
- •5.5 Server Error
- •5.5.1 500 Server Internal Error
- •5.5.2 501 Not Implemented
- •5.5.3 502 Bad Gateway
- •5.5.4 503 Service Unavailable
- •5.5.5 504 Gateway Timeout
- •5.5.6 505 Version Not Supported
- •5.5.7 513 Message Too Large
- •5.5.8 580 Preconditions Failure
- •5.6 Global Error
- •5.6.1 600 Busy Everywhere
- •5.6.2 603 Decline
- •5.6.3 604 Does Not Exist Anywhere
- •5.6.4 606 Not Acceptable
- •5.7 Questions
- •References
- •6 SIP Header Fields
- •6.1 Request and Response Header Fields
- •6.1.1 Accept
- •6.1.2 Accept-Encoding
- •6.1.3 Accept-Language
- •6.1.4 Alert-Info
- •6.1.5 Allow
- •6.1.6 Allow-Events
- •6.1.7 Answer-Mode
- •6.1.8 Call-ID
- •6.1.9 Contact
- •6.1.10 CSeq
- •6.1.11 Date
- •6.1.12 Encryption
- •6.1.13 Expires
- •6.1.14 From
- •6.1.15 History Info
- •6.1.16 Organization
- •6.1.17 Path
- •6.1.19 Record-Route
- •6.1.20 Recv-Info
- •6.1.21 Refer-Sub
- •6.1.22 Retry-After
- •6.1.23 Subject
- •6.1.24 Supported
- •6.1.25 Timestamp
- •6.1.27 User-Agent
- •6.2 Request Header Fields
- •6.2.1 Accept-Contact
- •6.2.2 Authorization
- •6.2.3 Call-Info
- •6.2.4 Event
- •6.2.5 Hide
- •6.2.6 Identity
- •6.2.7 Identity-Info
- •6.2.8 In-Reply-To
- •6.2.9 Info-Package
- •6.2.10 Join
- •6.2.11 Priority
- •6.2.12 Privacy
- •6.2.13 Proxy-Authorization
- •6.2.14 Proxy-Require
- •6.2.15 P-OSP-Auth-Token
- •6.2.16 P-Asserted-Identity
- •6.2.17 P-Preferred-Identity
- •6.2.18 Max-Breadth
- •6.2.19 Max-Forwards
- •6.2.20 Reason
- •6.2.21 Refer-To
- •6.2.22 Referred-By
- •6.2.23 Reply-To
- •6.2.24 Replaces
- •6.2.25 Reject-Contact
- •6.2.26 Request-Disposition
- •6.2.27 Require
- •6.2.28 Resource-Priority
- •6.2.29 Response-Key
- •6.2.30 Route
- •6.2.31 RAck
- •6.2.32 Security-Client
- •6.2.33 Security-Verify
- •6.2.34 Session-Expires
- •6.2.35 SIP-If-Match
- •6.2.36 Subscription-State
- •6.2.37 Suppress-If-Match
- •6.2.38 Target-Dialog
- •6.2.39 Trigger-Consent
- •6.3 Response Header Fields
- •6.3.1 Accept-Resource-Priority
- •6.3.2 Authentication-Info
- •6.3.3 Error-Info
- •6.3.4 Flow-Timer
- •6.3.5 Min-Expires
- •6.3.7 Permission-Missing
- •6.3.8 Proxy-Authenticate
- •6.3.9 Security-Server
- •6.3.10 Server
- •6.3.11 Service-Route
- •6.3.12 SIP-ETag
- •6.3.13 Unsupported
- •6.3.14 Warning
- •6.3.15 WWW-Authenticate
- •6.3.16 RSeq
- •6.4 Message Body Header Fields
- •6.4.1 Content-Encoding
- •6.4.2 Content-Disposition
- •6.4.3 Content-Language
- •6.4.4 Content-Length
- •6.4.5 Content-Type
- •6.4.6 MIME-Version
- •6.5 Questions
- •References
- •7 Wireless, Mobility, and IMS
- •7.1 IP Mobility
- •7.2 SIP Mobility
- •7.4 IMS Header Fields
- •7.5 Conclusion
- •7.6 Questions
- •References
- •8 Presence and Instant Messaging
- •8.1 Introduction
- •8.2 History of IM and Presence
- •8.3 SIMPLE
- •8.4 Presence with SIMPLE
- •8.4.1 SIP Events Framework
- •8.4.2 Presence Bodies
- •8.4.3 Resource Lists
- •8.4.4 Filtering
- •8.4.6 Partial Publication
- •8.4.7 Presence Documents Summary
- •8.5 Instant Messaging with SIMPLE
- •8.5.1 Page Mode Instant Messaging
- •8.5.4 Message Composition Indication
- •8.5.5 Multiple Recipient Messages
- •8.5.6 Session Mode Instant Messaging
- •8.6 Jabber
- •8.6.1 Standardization as Extensible Messaging and Presence Protocol
- •8.6.2 Interworking with SIMPLE
- •8.6.3 Jingle
- •8.6.4 Future Standardization of XMPP
- •8.7 Conclusion
- •8.8 Questions
- •References
- •9 Services in SIP
- •9.1 Gateway Services
- •9.2 SIP Trunking
- •9.3 SIP Service Examples
- •9.4 Voicemail
- •9.5 SIP Video
- •9.6 Facsimile
- •9.7 Conferencing
- •9.7.1 Focus
- •9.7.2 Mixer
- •9.8 Application Sequencing
- •9.9 Other SIP Service Architectures
- •9.9.1 Service Oriented Architecture
- •9.9.2 Servlets
- •9.9.3 Service Delivery Platform
- •9.10 Conclusion
- •9.11 Questions
- •References
- •10 Network Address Translation
- •10.1 Introduction to NAT
- •10.2 Advantages of NAT
- •10.3 Disadvantages of NAT
- •10.4 How NAT Works
- •10.5 Types of NAT
- •10.5.1 Endpoint Independent Mapping NAT
- •10.5.2 Address Dependent Mapping NAT
- •10.5.3 Address and Port Dependent Mapping NAT
- •10.5.4 Hairpinning Support
- •10.5.5 IP Address Pooling Options
- •10.5.6 Port Assignment Options
- •10.5.7 Mapping Refresh
- •10.5.8 Filtering Modes
- •10.6 NAT Mapping Examples
- •10.7 NATs and SIP
- •10.8 Properties of a Friendly NAT or How a NAT Should BEHAVE
- •10.9 STUN Protocol
- •10.10 UNSAF Requirements
- •10.11 SIP Problems with NAT
- •10.11.1 Symmetric SIP
- •10.11.2 Connection Reuse
- •10.11.3 SIP Outbound
- •10.12 Media NAT Traversal Solutions
- •10.12.1 Symmetric RTP
- •10.12.2 RTCP Attribute
- •10.12.3 Self-Fixing Approach
- •10.13 Hole Punching
- •10.14 TURN: Traversal Using Relays Around NAT
- •10.15 ICE: Interactive Connectivity Establishment
- •10.16 Conclusion
- •10.17 Questions
- •References
- •11 Related Protocols
- •11.1 PSTN Protocols
- •11.1.1 Circuit Associated Signaling
- •11.1.2 ISDN Signaling
- •11.1.3 ISUP Signaling
- •11.2 SIP for Telephones
- •11.3 Media Gateway Control Protocols
- •11.4.1 Introduction to H.323
- •11.4.2 Example of H.323
- •11.4.3 Versions
- •References
- •12 Media Transport
- •12.1 Real-Time Transport Protocol (RTP)
- •12.2 RTP Control Protocol (RTCP)
- •12.2.1 RTCP Reports
- •12.2.2 RTCP Extended Reports
- •12.3 Compression
- •12.4.1 Audio Codecs
- •12.4.2 Video Codecs
- •12.5 Conferencing
- •12.6 ToIP—Conversational Text
- •12.7 DTMF Transport
- •12.8 Questions
- •References
- •13 Negotiating Media Sessions
- •13.1 Session Description Protocol (SDP)
- •13.1.1 Protocol Version
- •13.1.2 Origin
- •13.1.3 Session Name and Information
- •13.1.5 E-Mail Address and Phone Number
- •13.1.6 Connection Data
- •13.1.7 Bandwidth
- •13.1.8 Time, Repeat Times, and Time Zones
- •13.1.9 Encryption Keys
- •13.1.10 Media Announcements
- •13.1.11 Attributes
- •13.2 SDP Extensions
- •13.3 The Offer Answer Model
- •13.3.1 Rules for Generating an Offer
- •13.3.2 Rules for Generating an Answer
- •13.3.3 Rules for Modifying a Session
- •13.3.4 Special Case—Call Hold
- •13.4 Static and Dynamic Payloads
- •13.5 SIP Offer Answer Exchanges
- •13.6 Conclusion
- •13.7 Questions
- •References
- •14 SIP Security
- •14.1 Basic Security Concepts
- •14.1.1 Encryption
- •14.1.2 Public Key Cryptography
- •14.1.4 Message Authentication
- •14.2 Threats
- •14.3 Security Protocols
- •14.3.1 IPSec
- •14.3.3 DNSSec
- •14.3.4 Secure MIME
- •14.4 SIP Security Model
- •14.4.1 SIP Digest Authentication
- •14.4.2 SIP Authentication Using TLS
- •14.4.3 Secure SIP
- •14.4.4 Identity
- •14.4.5 Enhanced SIP Identity
- •14.6 Media Security
- •14.6.1 Non-RTP Media
- •14.6.2 Secure RTP
- •14.6.3 Keying SRTP
- •14.6.4 Best Effort Encryption
- •14.6.5 ZRTP
- •14.7 Questions
- •References
- •15 Peer-to-Peer SIP
- •15.1 P2P Properties
- •15.2 P2P Properties of SIP
- •15.3 P2P Overlays
- •15.4 RELOAD
- •15.5 Host Identity Protocol
- •15.6 Conclusion
- •15.7 Questions
- •References
- •16 Call Flow Examples
- •16.1 SIP Call with Authentication, Proxies, and Record-Route
- •16.2 SIP Call with Stateless and Stateful Proxies with Called Party Busy
- •16.3 SIP to PSTN Call Through Gateways
- •16.4 PSTN to SIP Call Through a Gateway
- •16.5 Parallel Search
- •16.6 Call Setup with Two Proxies
- •16.7 SIP Presence and Instant Message Example
- •References
- •17 Future Directions
- •17.2 More Extensions
- •17.3 Better Identity
- •17.4 Interdomain SIP
- •17.5 Making Features Work Better
- •17.6 Emergency Calling
- •17.7 More SIP Trunking
- •17.9 Improved NAT Traversal
- •17.10 Security Deployment
- •17.11 Better Interoperability
- •References
- •A.1 ABNF Rules
- •A.2 Introduction to XML
- •References
- •About the Author
64 |
SIP: Understanding the Session Initiation Protocol |
same time. For contacts with different priorities, a proxy can do sequential forking, sending the request in the order specified by the q-values.
For full registration security, TLS must be used as HTTP digest does not provide the needed integrity protection. Otherwise, an attacker can modify the Contact URI in an authenticated REGISTER to point to another UA.
3.6 Uniform Resource Indicators
SIP uses a number of Uniform Resource Identifiers. Common URIs are shown in Table 3.2.
SIP URIs will be discussed in Section 4.2. SIPS will be covered in Chapter 14. Telephony URI is covered in Section 4.2.2. Presence and IM URIs are covered in Chapter 8, along with the XMPP URI. H.323 URIs are covered in Section 11.4. Web URIs are defined in [10].
SIP uses Uniform Resource Indicators or URIs for most addresses. URIs and URLs were introduced in Section 1.4. For SIP, the URI scheme is either sip for a normal SIP URI or sips for a Secure SIP URI. Secure SIP means that a SIP message sent using this URI will be protected using TLS across each hop. SIP URIs must contain either a host name or an IP address. They usually contain a user part, although they do not have to. For example, a URI for a proxy server typically will not have a user part. URIs also may contain parameters. SIP URI parameters are listed in Table 3.3. In this table, URI means any valid URI while URN means any valid URN.
The following is a list of some examples of SIP URIs.
sip:fred@flintstone.org sip:vilma@flintstone.org;transport=tcp sip:the%20great%one@whalers.org sip:7325551212@gw.gateway.com sip:192.0.3.4:44352 sip:proxy34.sipstation.com
Table 3.2
Common URIs Used with SIP
URI Scheme |
Use |
Specification |
|
|
|
sip |
SIP |
RFC 3261 |
sips |
Secure SIP |
RFC 3261 |
tel |
Telephony |
RFC 3966 |
pres |
Presence |
RFC 3861 |
im |
Instant messaging |
RFC 3861 |
xmpp |
XMPP (Jabber) |
RFC 4622 |
h323 |
H.323 |
RFC 3508 |
http |
Web |
RFC 2616 |
|
|
SIP Clients and Servers |
65 |
|
|
|
|
Table 3.3 |
|
|
|
|
SIP URI Parameters |
|
|
Parameter |
Specification |
Example |
Common Usage |
|
|
|
|
|
|
cause |
RFC 4458 |
cause=486 |
Voicemail |
|
comp |
RFC 3486 |
comp=sigcomp |
Sigcomp compression used |
|
content-type |
RFC 4240 |
content-type=audio |
Media server control |
|
delay |
RFC 4240 |
delay=10 |
Media server control |
|
duration |
RFC 4240 |
duration=60 |
Media server control |
|
gr |
[14] |
gr |
Globally routable UA URI |
|
local |
RFC 4240 |
local=en |
Media server control |
|
lr |
RFC 3261 |
lr |
Loose route parameter used in |
|
Route and Record-Route |
|||
|
|
|
|
|
|
maddr |
RFC 3261 |
maddr=1.2.3.4 |
Multicast address |
|
method |
RFC 3261 |
method=INVITE |
Used to escape a method into |
|
a URI |
|||
|
|
|
|
|
|
ob |
[15] |
ob |
SIP outbound |
|
param[n] |
RFC 4240 |
param1=”today” |
Media server control [11] |
|
play |
RFC 4240 |
play=URI |
Media server control [11] |
|
repeat |
RFC 4240 |
repeat=forever |
Media server control [11] |
|
sigcomp-id |
RFC 5049 |
sigcomp-id=URN |
Sigcomp ID [12] |
|
target |
RFC 4240 |
target=IRO |
Media server control [11] |
|
target |
RFC 4458 |
target=URI |
Voicemail [13] |
|
ttl |
RFC 3261 |
ttl=224 |
Time to live for a multicast |
|
address |
|||
|
|
|
|
|
|
transport |
RFC 3261 |
transport=tcp |
Transport protocol |
|
user |
RFC 3261 |
user=phone |
Telephone digits in user part |
|
voicexml |
RFC 4240 |
voicexml=URI |
Media server control [11] |
sip:r3.example.com;lr
sip:+43321232;user=phone@sp.serviceprovider.org
SIP URIs can also be used to encoded telephone numbers. Sometimes, this includes the user=phone parameter.
3.7 Acknowledgment of Messages
Most SIP requests are end-to-end messages between user agents. Proxies between the two user agents simply forward the messages they receive and rely on the user agents to generate acknowledgments or responses.
There are some exceptions to this general rule. The CANCEL method (used to terminate pending calls or searches and discussed in detail in Section 4.1.5) is a hop-by-hop request. A proxy receiving a CANCEL immediately sends a 200 OK response back to the sender and generates a new CANCEL, which is then forwarded in the next hop to the same set of destinations as the original request. (The order

66 SIP: Understanding the Session Initiation Protocol
of sending the 200 OK and forwarding the CANCEL is not important.) This is shown in Figure 3.4.
Other exceptions to this rule include 3xx, 4xx, 5xx, and 6xx responses to an INVITE request. While an ACK to a 2xx response is generated by the end point, a 3xx, 4xx, 5xx, or 6xx response is acknowledged on a hop-by-hop basis. A proxy server receiving one of these responses immediately generates an ACK back to the sender and forwards the response to the next hop. This type of hop-by- hop acknowledgment is shown in Figure 4.2.
ACK messages are only sent to acknowledge responses to INVITE requests. For responses to all other request types, there is no acknowledgment. A lost response is detected by the UAS when the request is retransmitted.
3.8 Reliability
SIP has reliability mechanisms defined, which allow the use of unreliable transport layer protocols such as UDP. When SIP uses TCP, these mechanisms are not used, since it is assumed that TCP will retransmit the message if it is lost and inform the client if the server is unreachable.
For SIP transport using UDP, there is always the possibility of messages being lost or even received out of sequence, because UDP guarantees only that the datagram is error free. A UAS validates and parses a SIP request to make sure that the UAC has not errored by creating a request missing required header fields or other syntax violations. Reliability mechanisms in SIP include:
•Retransmission timers;
•Increasing command sequence CSeq numbers;
•Positive acknowledgments.
How SIP handles retransmissions depends on the method. One retransmission scheme is defined for INVITEs, known as INVITE transactions, and another is defined for all other methods, known as a non-INVITE transaction.
For non-INVITE transactions, a SIP timer, T1, is started by a UAC or a stateful proxy server when a new request is generated or sent. If no response to the request (as identified by a response containing the identical local tag, remote tag, Call-ID, and CSeq) is received when T1 expires, the request is resent. After a request is retransmitted, the next timer period is doubled until T2 is reached. If a provisional (informational class 1xx) response is received, the UAC or stateful proxy server immediately switches to timer T2. After that, the remaining retransmissions occur at T2 intervals. This capped exponential backoff process is continued until a 64*T1, after which the request is declared dead. A stateful proxy
SIP Clients and Servers |
67 |
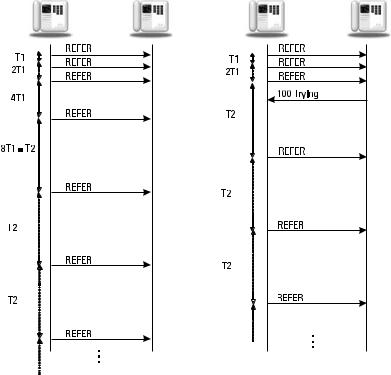
server that receives a retransmission of a request discards the retransmission and continues its retransmission schedule based on its own timers. Typically, it will resend the last provisional response. This retransmission scheme for non-INVITE is shown in Figure 3.6 for a REFER request.
For an INVITE transaction, the retransmission scheme is slightly different. INVITEs are retransmitted starting at T1, and then the timer is doubled after each retransmission. The INVITE is retransmitted until 64*T1 after which the request is declared dead. After a provisional (1xx) response is received, the INVITE is never retransmitted. This retransmission scheme is shown in Figure 3.7. A proxy may discard the transaction state after 3 minutes. A stateful proxy must store a forwarded request or generated response message for 32 seconds. Suggested default values for T1 and T2 are 500 ms and 4 seconds, respectively. Timer T1 is supposed to be an estimate of the roundtrip time (RTT) in the network. Longer values are allowed, but not shorter ones, because this will generate more message retransmissions. See Table 4 in RFC 3261 [1] for a summary of SIP timers.
Note that gaps in CSeq number do not always indicate a lost message. In the authentication examples, not every request (and hence CSeq) generated by
Figure 3.6 A SIP reliability example of a non-INVITE transaction.
