
- •CCIE Security Written Exam Blueprint
- •General Networking Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Networking Basics—The OSI Reference Model
- •Ethernet Overview
- •Internet Protocol
- •Variable-Length Subnet Masks
- •Classless Interdomain Routing
- •Transmission Control Protocol
- •TCP Services
- •Routing Protocols
- •ISDN
- •IP Multicast
- •Asynchronous Communications and Access Devices
- •Foundation Summary
- •Requirements for FastEther Channel
- •Scenario
- •Scenario 2-1: Routing IP on Cisco Routers
- •Scenario Answers
- •Scenario 2-1 Answers: Routing IP on Cisco Routers
- •Application Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Domain Name System
- •Trivial File Transfer Protocol
- •File Transfer Protocol
- •Hypertext Transfer Protocol
- •Secure Socket Layer
- •Simple Network Management Protocol
- •Simple Mail Transfer Protocol
- •Network Time Protocol
- •Secure Shell
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Scenario 3-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Cisco Hardware
- •show and debug Commands
- •Password Recovery
- •Basic Security on Cisco Routers
- •IP Access Lists
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Security Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Authentication, Authorization, and Accounting (AAA)
- •Remote Authentication Dial-In User Service (RADIUS)
- •Kerberos
- •Virtual Private Dial-Up Networks (VPDN)
- •Encryption Technology Overview
- •Internet Key Exchange (IKE)
- •Foundation Summary
- •Scenario
- •Scenario 5-1: Configuring Cisco Routers for IPSec
- •Scenario Answers
- •Scenario 5-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •UNIX
- •Microsoft NT Systems
- •Common Windows DOS Commands
- •Cisco Secure for Windows and UNIX
- •Cisco Secure Policy Manager
- •Cisco Secure Intrusion Detection System and Cisco Secure Scanner
- •Cisco Security Wheel
- •Foundation Summary
- •Scenarios
- •Scenario 6-1: NT File Permissions
- •Scenario 6-2: UNIX File Permissions
- •Scenario Answers
- •Scenario 6-1 Solution
- •Scenario 6-2 Solution
- •Security Technologies
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Advanced Security Concepts
- •Cisco Private Internet Exchange (PIX)
- •Cisco IOS Firewall Security Feature Set
- •Public Key Infrastructure
- •Virtual Private Networks
- •Foundation Summary
- •Scenario
- •Scenario Answer
- •Scenario 7-1 Solution
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Network Security Policies
- •Standards Bodies and Incident Response Teams
- •Vulnerabilities, Attacks, and Common Exploits
- •Intrusion Detection System
- •Protecting Cisco IOS from Intrusion
- •Foundation Summary
- •Scenario
- •Scenario 8-1: Defining IOS Commands to View DoS Attacks in Real Time
- •Scenario Answer
- •Scenario 8-1 Solution

Kerberos 225
Example 5-9 displays a sample output from the debug aaa authentication command for a RADIUS login attempt that failed. The information indicates that TACACS is the authentication method used.
Example 5-9 debug aaa authentication
R1# debug aaa authentication
14:02:55: AAA/AUTHEN (164826761): Method=RADIUS 14:02:55: AAA/AUTHEN (164826761): status = GETPASS 14:03:01: AAA/AUTHEN/CONT (164826761): continue_login 14:03:01: AAA/AUTHEN (164826761): status = GETPASS 14:03:04: AAA/AUTHEN (164826761): status = FAIL
Example 5-10 displays a sample output from the debug radius command that shows a successful login attempt, as indicated by an Access-Accept message:
Example 5-10 debug radius Failure
R1# debug radius |
|
|
|
|
|
13:59:02: Radius: IPC Send |
0.0.0.0:1645, Access-Request, id 0xB, len 56 |
||||
13:59:02: |
Attribute |
4 |
6 |
AC150E5A |
|
13:59:02: |
Attribute |
5 |
6 |
0000000A |
|
13:59:02: |
Attribute |
1 |
6 |
62696C6C |
|
13:59:02: |
Attribute |
2 |
18 0531FEA3 |
||
13:59:04: Radius: Received from |
131.108.1.1:1645, |
Access-Accept, id 0xB, len 26 |
|||
13:59:04: |
Attribute |
6 |
6 |
00000001 |
|
|
|
|
|
|
|
Example 5-11 displays a sample output from the debug radius command that shows an unsuccessful login attempt, as indicated by an Access-Reject message.
Example 5-11 debug radius Command
R1# debug radius
13:57:56: Radius: IPC Send 0.0.0.0:1645, Access-Request, id 0xA, len 57 13:57:56: Attribute 4 6 AC150E5A
13:57:56: Attribute 5 6 0000000A
13:57:56: Attribute 1 7 62696C6C
13:57:56: Attribute 2 18 49C28F6C
13:57:59: Radius: Received from 171.69.1.152:1645, Access-Reject, id 0xA, len 20
Kerberos
Kerberos is a trusted third-party authentication application layer service (Layer 7 of the OSI model).
Kerberos is a secret-key network authentication protocol developed at the Massachusetts Institute of Technology (MIT) that uses the Data Encryption Standard (DES) cryptographic
226 Chapter 5: Security Protocols
algorithm for encryption and authentication. In the Kerberos protocol, this trusted third party is called the key distribution center (KDC).
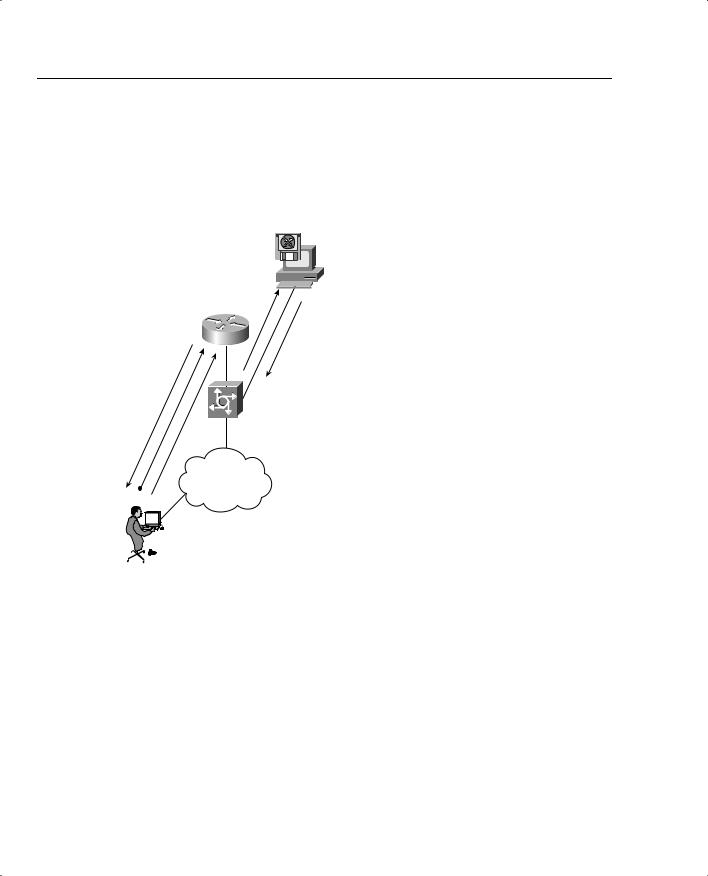
Figure 5-4 displays the Kerberos authentication process when a remote client initiates a remote Telnet session. (Kerberos supports Telnet, rlogin, rsh, and rcp.)
Figure 5-4 Authentication Service with Kerberos
R1
4.
2.
Network
Access
Server
IP
6. 5. Network
1.
User: Simon
Key Distribution
Center (KDC)
3.
Authentication Process
•User initiates Telnet session to Router R1.
•The NAS builds a Service credential request and sends it to the KDC.
•KDC decrypts the request and builds service credential, sends to user Simon.
•User Simon decrypts.
•R1 decrypts credential.
•User Simon exchanges data with Router R1.
Kerberos’s primary use is to verify that users and the network services they employ are really who and what they claim to be. To accomplish this, a trusted Kerberos server issues tickets to users. These tickets, which have a limited lifespan, are stored in a user’s credential cache and can be used in place of the standard username/password authentication mechanism.
The Kerberos credential scheme embodies a concept called single logon. This process requires authenticating a user once, and then allows secure authentication (without encrypting another password) wherever that user’s credential is accepted.
Timestamps (large numbers representing the current date and time) have been added to the original Kerberos model to aid in the detection of replay attacks. Replay attacks basically reply to data flow with an unauthorized source attempting to gain access to a host. During the packet flow exchange, critical parameters exchanged are the client’s name, the IP address, and the

|
|
|
Kerberos 227 |
|
|
|
|
|
current workstation time. System time must be accurate to ensure replay attacks are avoided or, |
||
|
at the very least, detected, and the Kerberos session terminated. |
||
|
|
|
|
NOTE |
Starting with Cisco IOS Release 11.2, Cisco IOS Software includes Kerberos 5 support, which |
||
|
allows organizations already deploying Kerberos 5 to use the same Kerberos authentication |
||
|
database on their routers that they already use on their other network hosts (such as UNIX |
||
|
servers and PCs). |
|
|
|
|
|
|
|
Table 5-5 summarizes the key concepts of Kerberos. |
||
Table 5-5 |
Features of the Kerberos Protocol |
||
|
|
|
|
|
Feature |
Description |
|
|
|
|
|
|
Packet delivery |
A number of ports are defined: TCP/UDP ports 88, 543, 749, and TCP ports |
|
|
|
754, 2105, and 4444. |
|
|
|
|
|
|
Packet encryption |
Supports username/password encryption. |
|
|
|
|
|
|
Telnet support |
Telnet sessions can be encrypted. |
|
|
|
|
|
|
Table 5-6 defines common Kerberos terminology. |
||
Table 5-6 |
Kerberos Terminology |
|
|
|
|
|
|
|
Term |
|
Definition |
|
|
|
|
|
Credential |
|
A general term that refers to authentication tickets, such as ticket granting |
|
|
|
tickets (TGTs) and service credentials. Kerberos credentials verify the |
|
|
|
identity of a user or service. If a network service decides to trust the |
|
|
|
Kerberos server that issued a ticket, it can be used in place of retyping in a |
|
|
|
username and password. Credentials have a default lifespan of eight hours. |
|
|
|
|
|
Instance |
|
An authorization level label for Kerberos principals. Most Kerberos princi- |
|
|
|
pals are of the form user@REALM (for example, smith@EXAMPLE.COM). |
|
|
|
Note that the Kerberos realm name must be in uppercase characters. |
|
|
|
|
|
Kerberized |
|
Applications and services that have been modified to support the Kerberos |
|
|
|
credential infrastructure. |
|
|
|
|
|
Kerberos realm |
|
A domain consisting of users, hosts, and network services that are regis- |
|
|
|
tered to a Kerberos server. The Kerberos server is trusted to verify a user’s |
|
|
|
or network service’s identity to another user or network service. Kerberos |
|
|
|
realms must always be in uppercase characters. TCP fragmentation must |
|
|
|
also be defined on the key distribution center (KDC) server. The Kerberos |
|
|
|
realm is also used to map a DNS domain to a Kerberos realm. |
|
|
|
|
continues

228 Chapter 5: Security Protocols
Table 5-6 |
Kerberos Terminology (Continued) |
|
|
|
|
|
Term |
Definition |
|
|
|
|
Kerberos server |
A daemon running on a network host. Users and network services register |
|
|
their identities with the Kerberos server. Network services query the |
|
|
Kerberos server to authenticate to other network services. Also known as |
|
|
the Master Kerberos server. |
|
|
|
|
Key Distribution Center |
A Kerberos server and database program running on a network host. |
|
(KDC) |
|
|
|
|
|
Principal |
Also known as a Kerberos identity, this is who you are or what a service is |
|
|
according to the Kerberos server. |
|
|
|
|
Service credential |
A credential for a network service. When issued from the KDC, this |
|
|
credential is encrypted with the password shared by the network service and |
|
|
the KDC, and with the user’s TGT. |
|
|
|
|
SRVTAB |
A password that a network service shares with the KDC. The network |
|
|
service authenticates an encrypted service credential using the SRVTAB |
|
|
(also known as a KEYTAB) to decrypt it. |
|
|
|
|
Ticket Granting Ticket |
A credential that the KDC issues to authenticated users. When users receive |
|
(TGT) |
a TGT, they can authenticate to network services within the Kerberos realm |
|
|
represented by the KDC. |
|
|
|
Kerberos Configuration Task List
To configure Kerberos support on a Cisco router, complete the following tasks:
Step 1 Define the default realm for the router:
kerberos local-realm kerberos-realm
Step 2 Specify to the router which KDC to use in a given Kerberos realm and, optionally, the port number that the KDC is monitoring. (The default port number is 88.)
kerberos server kerberos-realm {hostname | ip-address} [port-number]
Step 3 Map a host name or DNS domain to a Kerberos realm (optional):
kerberos realm {dns-domain | host} kerberos-realm
NOTE The kerberos local-realm, kerberos realm, and kerberos server commands are equivalent to the UNIX krb.conf file.
