
- •CCIE Security Written Exam Blueprint
- •General Networking Topics
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Networking Basics—The OSI Reference Model
- •Ethernet Overview
- •Internet Protocol
- •Variable-Length Subnet Masks
- •Classless Interdomain Routing
- •Transmission Control Protocol
- •TCP Services
- •Routing Protocols
- •ISDN
- •IP Multicast
- •Asynchronous Communications and Access Devices
- •Foundation Summary
- •Requirements for FastEther Channel
- •Scenario
- •Scenario 2-1: Routing IP on Cisco Routers
- •Scenario Answers
- •Scenario 2-1 Answers: Routing IP on Cisco Routers
- •Application Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Domain Name System
- •Trivial File Transfer Protocol
- •File Transfer Protocol
- •Hypertext Transfer Protocol
- •Secure Socket Layer
- •Simple Network Management Protocol
- •Simple Mail Transfer Protocol
- •Network Time Protocol
- •Secure Shell
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Scenario 3-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Cisco Hardware
- •show and debug Commands
- •Password Recovery
- •Basic Security on Cisco Routers
- •IP Access Lists
- •Foundation Summary
- •Scenario
- •Scenario Answers
- •Security Protocols
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Authentication, Authorization, and Accounting (AAA)
- •Remote Authentication Dial-In User Service (RADIUS)
- •Kerberos
- •Virtual Private Dial-Up Networks (VPDN)
- •Encryption Technology Overview
- •Internet Key Exchange (IKE)
- •Foundation Summary
- •Scenario
- •Scenario 5-1: Configuring Cisco Routers for IPSec
- •Scenario Answers
- •Scenario 5-1 Solutions
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •UNIX
- •Microsoft NT Systems
- •Common Windows DOS Commands
- •Cisco Secure for Windows and UNIX
- •Cisco Secure Policy Manager
- •Cisco Secure Intrusion Detection System and Cisco Secure Scanner
- •Cisco Security Wheel
- •Foundation Summary
- •Scenarios
- •Scenario 6-1: NT File Permissions
- •Scenario 6-2: UNIX File Permissions
- •Scenario Answers
- •Scenario 6-1 Solution
- •Scenario 6-2 Solution
- •Security Technologies
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Advanced Security Concepts
- •Cisco Private Internet Exchange (PIX)
- •Cisco IOS Firewall Security Feature Set
- •Public Key Infrastructure
- •Virtual Private Networks
- •Foundation Summary
- •Scenario
- •Scenario Answer
- •Scenario 7-1 Solution
- •“Do I Know This Already?” Quiz
- •Foundation Topics
- •Network Security Policies
- •Standards Bodies and Incident Response Teams
- •Vulnerabilities, Attacks, and Common Exploits
- •Intrusion Detection System
- •Protecting Cisco IOS from Intrusion
- •Foundation Summary
- •Scenario
- •Scenario 8-1: Defining IOS Commands to View DoS Attacks in Real Time
- •Scenario Answer
- •Scenario 8-1 Solution

320 Chapter 7: Security Technologies
Foundation Topics
Advanced Security Concepts
A wealth of security concepts have been covered and now some of the techniques used in areas of your network will be covered that are vulnerable to attacks, in particular, the Demilitarized Zone (DMZ).
The DMZ is defined as an isolated part of the network that is easily accessible to hosts outside of the network, such as the Internet.
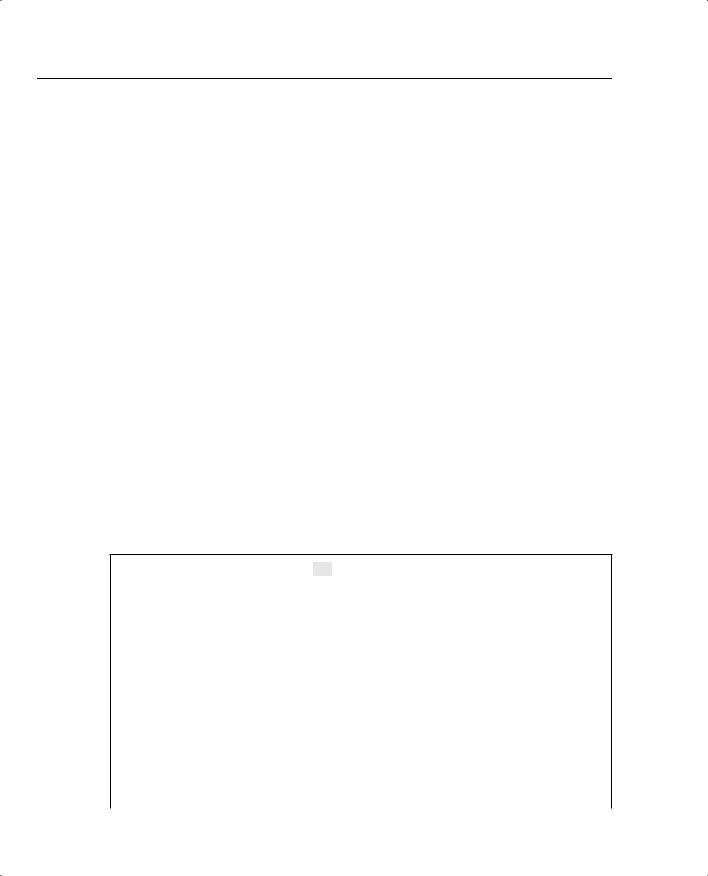
Figure 7-1 displays a typical network design where a DMZ is defined with a number of bastion hosts (first line of defense or hosts that can be scarified in case of a network attack or attacks).
Figure 7-1 DMZ Design
Perimeter or |
Bastion Hosts – |
Edge Router |
FTP Server, HTTP Server, |
|
Proxy Servers |
Internet
DMZ


 Firewalls
Firewalls 


Private
Network
Figure 7-1 displays a typical perimeter network where the DMZ is separated by a firewall. Firewalls are network devices such as Private Internet Exchange (PIX), which are discussed later in this chapter. Firewalls are designed to protect the internal (or private) parts of a network from the public domain.

Advanced Security Concepts 321
The aim of all firewalls is to accomplish the following:
•Serve as a traffic point—The traffic from inside and outside the network must pass through the traffic point.
•Authorize traffic—Permits only authorized traffic.
•Designed to be immune from penetration—Firewalls are designed to be immune from attacks. Firewalls are still often devices that are attacked by outside hosts.
•Invisibility—Ensures that the private network is invisible to the outside world.
As shown in Figure 7-1, the perimeter router sits between the DMZ and the public domain. Typically, a high performance router or routers will be located here, performing a number of duties including the following:
•Ensuring that access to the Internet Protocol (IP) is restricted using access lists
•Restricting Transmission Control Protocol (TCP) services
•Preventing attacks on firewall systems
•Preventing Denial of Service (DoS) attacks on bastion hosts and the private network
•Permitting only authorized traffic to the bastion hosts
•Logging all network events to external or internal systems
•Performing Address translation (NAT/PAT)
•Running static or dynamic routing protocols; Cisco PIX is limited to RIP and static routing.
NOTE Proxy servers are designed to shield internal devices from outside intruders by replacing the internal hosts’ IP addresses with its own IP address. Most new vendors now allow routers to act as proxy servers. Proxy servers have scalability and speed issues, as all packets must be examined and IP headers modified for packet delivery.
Firewalls and perimeter routers have the additional function of packet filtering. A packet filter is a device that inspects all incoming and outgoing packets based on IP source address, destination IP address, and protocol type, such as TCP or UDP. Based on configurable options, the filter decides whether to reject or allow traffic to pass through the device.
Table 7-1 summarizes the main functions of a perimeter and firewall router.
322 Chapter 7: Security Technologies
Table 7-1 |
Perimeter/Firewall Router Functions |
|
|
|
|
|
Protection Service |
Method |
|
|
|
|
Sniffer or snooping capabilities |
Control eavesdropping with the TCP/IP service and network layer |
|
|
encryption (IPSec). |
|
|
|
|
Control unauthorized access |
Use authentication, authorization, accounting (AAA), and Cisco |
|
|
Secure. Also, access-list filtering and PIX Firewall. |
|
|
|
|
Controlling session replay |
Control what TCP/IP sessions are authorized. |
|
|
Block SNMP, IP source routing, and finger services to outside hosts. |
|
|
|
|
Controlling inbound |
Filter internal address as the source from the outside world. |
|
connections |
Filter all private addresses. |
|
|
|
|
|
Filter Bootp, Trivial File Transfer Protocol (TFTP), and trace route |
|
|
commands. |
|
|
Allow TCP connections established from the inside network. |
|
|
Permit inbound traffic to DMZ only. |
|
|
|
|
Controlling outbound |
Allow only valid IP addresses to the outside world and filter |
|
connections |
remaining illegal addresses. |
|
|
|
|
Packet filtering |
Use predefined access lists that control the transmission of packets |
|
|
from any given interface, controlling Virtual Terminal lines, VTY, |
|
|
and access, and ensuring that routing updates are authenticated. |
|
|
|
Cisco IOS routers can filter TCP or UDP protocol types. Example 7-1 displays the number of TCP services you can filter on a Cisco IOS router using extended access lists.
Example 7-1 TCP Services Filtered on Cisco IOS Routers
R1(config)#access-list 100 permit tcp any any eq ?
<0-65535> |
Port number |
|
bgp |
Border Gateway Protocol (179) |
|
chargen |
Character generator |
(19) |
cmd |
Remote commands (rcmd, 514) |
|
daytime |
Daytime (13) |
|
discard |
Discard (9) |
|
domain |
Domain Name Service |
(53) |
echo |
Echo (7) |
|
exec |
Exec (rsh, 512) |
|
finger |
Finger (79) |
|
ftp |
File Transfer Protocol (21) |
|
ftp-data |
FTP data connections (used infrequently, 20) |
|
gopher |
Gopher (70) |
|
hostname |
NIC hostname server |
(101) |
ident |
Ident Protocol (113) |
|
irc |
Internet Relay Chat |
(194) |
klogin |
Kerberos login (543) |
|
kshell |
Kerberos shell (544) |
|

Advanced Security Concepts 323
Example 7-1 TCP Services Filtered on Cisco IOS Routers (Continued)
login |
Login (rlogin, 513) |
lpd |
Printer service (515) |
nntp |
Network News Transport Protocol (119) |
pim-auto-rp |
PIM Auto-RP (496) |
pop2 |
Post Office Protocol v2 (109) |
pop3 |
Post Office Protocol v3 (110) |
smtp |
Simple Mail Transport Protocol (25) |
sunrpc |
Sun Remote Procedure Call (111) |
syslog |
Syslog (514) |
tacacs |
TAC Access Control System (49) |
talk |
Talk (517) |
telnet |
Telnet (23) |
time |
Time (37) |
uucp |
Unix-to-Unix Copy Program (540) |
whois |
Nicname (43) |
www |
World Wide Web (HTTP, 80) |
|
|
Example 7-2 displays the extended access list when filtering services based on the UDP protocol suite of services.
Example 7-2 UDP Services Filtered on Cisco IOS Routers
R1(config)#access-list 101 permit udp any any eq ?
<0-65535> |
Port number |
biff |
Biff (mail notification, comsat, 512) |
bootpc |
Bootstrap Protocol (BOOTP) client (68) |
bootps |
Bootstrap Protocol (BOOTP) server (67) |
discard |
Discard (9) |
dnsix |
DNSIX security protocol auditing (195) |
domain |
Domain Name Service (DNS, 53) |
echo |
Echo (7) |
isakmp |
Internet Security Association and Key Management Protocol (500) |
mobile-ip |
Mobile IP registration (434) |
nameserver |
IEN116 name service (obsolete, 42) |
netbios-dgm |
NetBios datagram service (138) |
netbios-ns |
NetBios name service (137) |
netbios-ss |
NetBios session service (139) |
ntp |
Network Time Protocol (123) |
pim-auto-rp |
PIM Auto-RP (496) |
rip |
Routing Information Protocol (router, in.routed, 520) |
snmp |
Simple Network Management Protocol (161) |
snmptrap |
SNMP Traps (162) |
sunrpc |
Sun Remote Procedure Call (111) |
syslog |
System Logger (514) |
tacacs |
TAC Access Control System (49) |
talk |
Talk (517) |
tftp |
Trivial File Transfer Protocol (69) |
time |
Time (37) |
who |
Who service (rwho, 513) |
xdmcp |
X Display Manager Control Protocol (177) |

324 Chapter 7: Security Technologies
Examples 7-1 and 7-2 clearly allow a network administrator flexibility when designing perimeter security based on particular port numbers, as defined in RFC 1700.
Network Address Translation and Port Address
Translation
|
NAT is a router function, which allows it to translate the addresses of hosts behind a firewall. |
|
|
This also helps to overcome IP address shortage. It also provides security by hiding the entire |
|
|
network and their real IP addresses. |
|
|
NAT is typically used for internal IP networks that have unregistered (not globally unique) |
|
|
IP addresses. NAT translates these unregistered addresses into legal addresses on the outside |
|
|
(public) network. |
|
|
PAT provides additional address expansion but is less flexible than NAT. With PAT, one IP |
|
|
address can be used for up to 64,000 hosts by mapping several IP port numbers to one IP |
|
|
address. PAT is secure because the inside hosts’ source IP addresses are hidden from the outside |
|
|
world. The perimeter router typically provides the NAT or PAT function. |
|
|
NAT is defined in RFC 1631, www.ietf.org/rfc/rfc1631.txt. Cisco devices started supporting |
|
|
NAT in IOS versions 11.2 and higher. NAT basically provides the capability to retain your |
|
|
network’s original IP addressing scheme while translating that scheme into a valid Internet IP |
|
|
address to ensure that intruders never view your private address. |
|
|
|
|
NOTE |
IOS 12.0 and higher support full NAT functionality in all images. Version 11.2 and higher need |
|
|
“PLUS” image for a NAT feature set. |
|
|
|
|
|
NAT changes the Layer 3 address when the packet is sent out to the Internet. This is a function |
|
|
no other protocol will do (that is, alter the Layer 3 source address). |
|
|
For your review to fully prepare you for the exam, Table 7-2 explains some of the terminology |
|
|
used in a NAT environment. |
|
Table 7-2 |
NAT Terminology |
|
|
|
|
|
Term |
Meaning |
|
|
|
|
Inside local address |
An IP address that is assigned to a host on the internal network; that is, the logi- |
|
|
cal address that is not being advertised to the Internet. A local administrator gen- |
|
|
erally assigns this address. This address is NOT a legitimate Internet address. |
|
|
|
|
Inside global address |
A legitimate registered IP address, as assigned by the InterNIC. |
|
|
|
|
Outside local |
The IP address of a network’s outside host that is being translated as it appears |
|
address |
to the inside network. |
|
|
|
|
Outside global |
The IP address assigned to a host on the outside of the network that is being |
|
address |
translated by the host’s owner. |
|
|
|
Network Address Translation and Port Address Translation 325
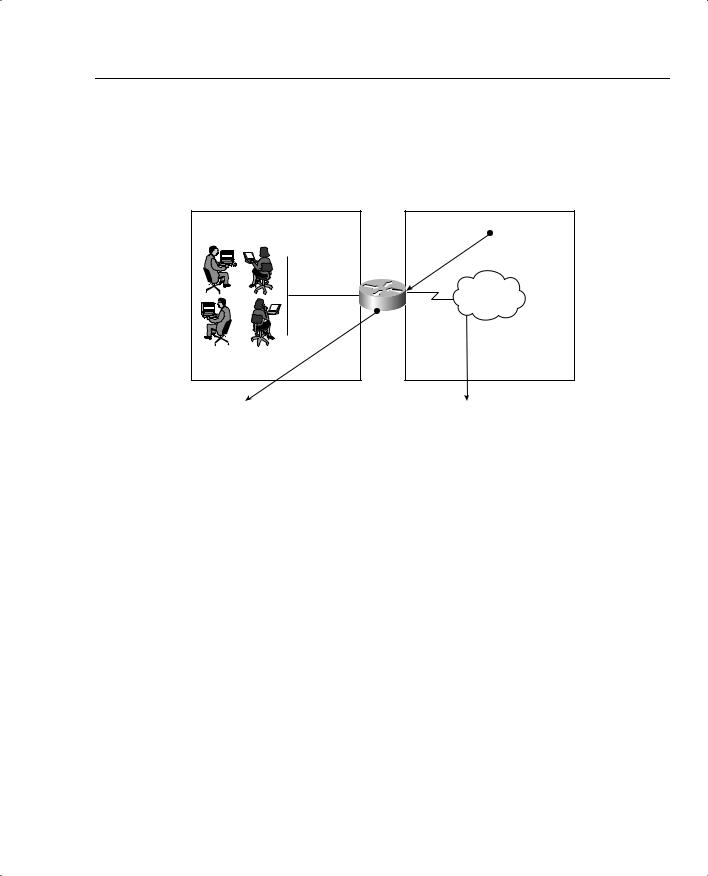
Figure 7-2 displays a typical scenario where a private address space is deployed that requires Internet access. The Class A 10.0.0.0/8 is not routable in the Internet.
Figure 7-2 Typical NAT Scenario
Inside or Private Network |
Outside Network |
|
131.108.1.1/24 |
10.99.34.0/24 |
Internet |
|
|
E0 |
S0 |
NAT Table |
InterNic Assigned Address |
Inside Address Outside Address |
210.1.1.0/24 |
10.99.34.1192.108.1.1
10.99.34.2192.108.1.2
... so on |
... and so on |
The users in Figure 7-2 are configured with the inside local addresses ranging from 10.99.34.1/24 to 10.99.34.254/24. To allow Internet access, NAT (PAT could also be configured if only one IP address was allocated by InterNIC) is configured on Router R1 to permit the inside local addresses access to the Internet. Advantages of using NAT include the following:
•You can hide the Class A address space 10.99.34.0/24
To view the NAT translation table on the Cisco router, apply the exec command show ip nat translations on the CLI interface.
•It gives you the capability to connect a nonroutable network to the Internet.
•You can use unregistered address space and NAT to the Internet.
•You can use both NAT/PAT on the same router.
•You can have 64,000 inside hosts per allocated IP address.
The InterNic is an Internet authority assigned the task of allocating IP address space to the public. In Figure 7-2, assume that the InterNIC assigned the address space 210.1.1.1/24 for use.

326 Chapter 7: Security Technologies
NOTE Disadvantages of NAT/PAT include the following:
•CPU processing power.
•Layer 3 header and source address changes.
•Voice over IP is not supported yet.
•Some Multimedia-intensive applications do not support NAT, especially when the data stream inbound is different from the outbound path (for example, in multicast environments).
NAT Operation on Cisco Routers
When a packet leaves the inside network, NAT translates the inside address to a unique InterNIC address for use on the outside network, as shown in Figure 7-2.
The R1 router in Figure 7-2 will be configured for an address translation and will maintain a NAT table. When an IP packet returns from the outside network, the NAT router will then perform an address translation from the valid InterNIC address to the original local inside address.
Dynamic NAT Configuration Task List
Look at the steps required to configure Dynamic NAT on a Cisco router. Dynamic NAT maps any unregistered IP addresses to a registered IP address from a group of registered IP addresses.
The basic configuration tasks are as follows:
1Determine the network addresses to be translated.
2Configure the inside network with the following IOS command:
ip nat inside
3 Configure the outside network with the following IOS command:
ip nat outside
4 Define a pool of addresses to be translated with the following IOS command:
ip nat pool <pool-name> <start ip address> <end ip address> <mask>
5Define the addresses that are allowed to access the Internet with the following IOS command:
ip nat inside source list <access list number> pool <pool name>

Network Address Translation and Port Address Translation 327
For a more specific illustration, configure NAT on Router R1. In Figure 7-2, the NAT pool name is going to be CCIE. (You can use any name you want.) Assume that the InterNIC has assigned you the Class C address of 210.1.1.0/2424.
Your Internet service provider (ISP) has also supplied you the unique address 131.108.1.1/30 to use on your serial connection.
Example 7-3 provides a sample NAT configuration for this setup.
Example 7-3 Sample NAT Configuration on R1
hostname R1
ip nat pool CCIE 210.1.1.1 210.1.1.254 netmask 255.255.255.0 ip nat inside source 1 pool CCIE
interface ethernet0
ip address 10.99.34.1 255.255.255.0 ip nat inside
interface serial 0
ip address 131.108.1.1 255.255.255.252
ip address 210.1.1.1 255.255.255.0 secondary ip nat outside
access-list 1 permit 10.99.34.0 0.0.0.255
It is assumed that you have an IP routing protocol to advertise the IP networks shown in the sample, which are 131.108.1.0/30 and 210.1.1.0/24, to the remote ISP router through R1’s Serial 0 interface.
The configuration shown in Example 7-3 translates the inside addresses 10.99.34.0/24 into globally unique addresses ranging from 210.1.1.1/24 to 210.1.1.254.
Monitoring NAT Operations with show Commands
To monitor the operation of NAT, you can use the following commands:
show ip nat translation [verbose] show ip nat statistics
The show ip nat translation command displays the current active transactions. The show ip nat statistics command displays NAT statistics, such as how many translations are currently taking place.
There are four different versions of NAT translations:
•Static NAT—Maps an unregistered IP address to a registered IP address on a one-to-one basis. This is particularly useful when a device needs to be accessible from outside the network to an internal unregistered address.
•Dynamic NAT—Maps an unregistered IP address to a registered IP address from a group of registered IP addresses.
