
20411B-ENU-TrainerHandbook
.pdf
Administering Windows Server® 2012 2-3
include .com, .net, .org, .biz, and .ca. The most recognized domains are .com, .net, .org, and .gov, which is for the government of the United States. There are several more domain names at this level, and there is a TLD for each country. For example, the TLD for Canada is .ca, and the TLD for the United Kingdom is .uk.
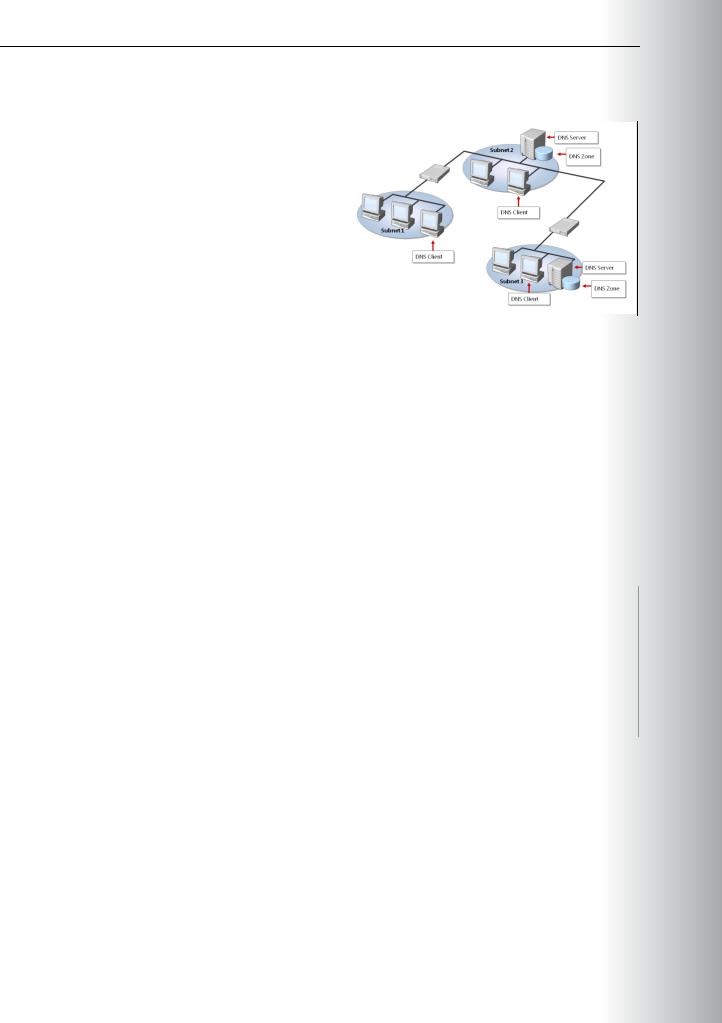
Overview of the DNS Namespace |
MCT |
|||
The DNS namespace facilitates how a DNS |
|
|||
|
|
|
||
|
USE |
|||
resolver locates a computer. The namespace is |
|
|||
organized hierarchically to distribute information |
|
|||
across many servers. |
|
|||
Root Domain |
|
|||
A period (.) represents the root domain, and you |
|
|||
|
|
|
||
do not type it into a web browser. The period (.) is |
|
|
|
|
assumed. The next time that you type an address |
|
|
|
|
into a computer, try adding the period at the end |
|
|
|
|
(for example, www.microsoft.com.). There are 13 |
|
|
|
|
root domain servers worldwide. |
|
|
|
|
|
.ONLY |
|||
|
Note: When troubleshooting DNS, it is usual to specify the trailing period. |
|||
|
||||
|
||||
Top-Level Domain |
STUDENT |
|||
The top-level domain (TLD) is the first level of the DNS name space. Examples of TLDs on the Internet |
||||
|
|
|
||
The organization that regulates domain names, known as the Internet Corporation for Assigned Names and Numbers (ICANN), adds new TLDs occasionally.
The second-level domain name is the portion of the domain name that appears before the TLD.
An example of a second-level domain name is microsoft in the www.microsoft.com domain. The organizations that register second-level domain names control them. Anyone may register a second-level domain name through an Internet registry service. Many second-level domains have special rules about
what organizations or people can register a domain name. For example, only nonprofit organizations mayUSE use .org.
PROHIBITED
•A through Z
•a through z
•0 through 9
•Hyphen (-)

2-4 Configuring and Troubleshooting Domain Name System
Note: The underscore (_) is a reserved character.
Integrating AD DS and DNS
When you begin planning your DNS namespace, you must consider both the internal and external namespaces. The internal namespace is the one that internal clients and servers use within your private network. The external namespace is the one by which your organization is referenced on the Internet. There is no requirement that you should implement the same DNS domain name internally that you have externally.
When you implement AD DS, you must use a DNS namespace for hosting AD DS records.
Note: Consider carefully your options
before selecting a namespace design for AD DS. Although it is possible to change a namespace after implementing AD DS, it is a time-consuming and complex process that has many limitations.
To determine a DNS namespace for your AD DS environment, you can choose from the following scenarios:
•Make the internal namespace the same as the public namespace. In this scenario, the internal and public namespaces are the same, but will have different records. Although this provides simplicity, which makes it a suitable choice for smaller organizations, it can be difficult to manage for larger networks.
•Make the internal namespace different from the public namespace. In this scenario, the internal and public namespaces are completely different, with no link between them. This provides for obvious separation in the namespace. In complex networks, with many Internet-facing applications, use of a different name introduces some clarity when configuring these applications. For example, Edge Servers that are placed on a perimeter network often require multiple network interface cards: one connected to the private network; and one servicing requests from the public network. If each network interface card has a different domain name, it often is easier to complete the configuration of that server.
•Make the internal namespace a subdomain of the public namespace. In this scenario, the internal namespace is linked to the public namespace, but there is no overlap between them. This provides a hybrid approach. The internal name is different, which allows for separation of the namespace. However, the internal name also is related to the public name, which provides simplicity. This approach is the simplest to implement and manage. However, if you cannot use a subdomain of the public namespace for AD DS, you should use unique namespaces.
PROHIBITED USE STUDENT .ONLY USE MCT

2MCT-5 USEONLY
STUDENT .
USE Having a matching internal and external DNS namespace can pose certain problems. However, split DNS
can provide a solution to these problems. Split DNS is a configuration in which your domain has two rootserver zones that contain domain-name registration information. Your internal network hosts are directed to one zone, while external hosts are directed to another for name resolution. For example, in a nonsplit DNS configuration for the domain Contoso.com, you might have a DNS zone that looks like the example in the following table.
Host |
Record type |
|
IP address |
PROHIBITED |
|
||||
|
|
|||
|
|
|
|
|
www |
A |
|
131.107.1.200 |
|
|
|
|
|
|
Relay |
A |
|
131.107.1.201 |
|
|
|
|
|
|
Webserver1 |
A |
|
192.168.1.200 |
|
|
|
|
|
|
Exchange1 |
A |
|
192.168.0.201 |
|
|
|
|
|
|

2-6
Host |
Record type |
IP address |
|
|
|
|
|
www |
CNAME |
Webserver1.contoso.com |
|
|
|
|
|
Relay |
CNAME |
Exchange1.contoso.com |
|
|
|
|
|
Webserver1 |
A |
192.168.1.200 |
|
|
|
|
|
Exchange1 |
A |
192.168.0.201 |
|
|
|
|
The external zone for adatum.com would resemble the information in the following table.
Host |
Record type |
IP address |
|
|
|
|
|
www |
A |
131.107.1.200 |
|
|
|
|
|
Relay |
A |
131.107.1.201 |
|
|
|
|
|
|
MX |
Relay.contoso.com |
|
|
|
|
Now, client computers in the internal and external networks can resolve the name relay.contoso.com to the appropriate internal or external IP address.
Demonstration: Installing the DNS Server Role
This demonstration shows how to install the DNS server role.
Demonstration Steps
1.Switch to LON-SVR1, and sign in as Adatum\Administrator with the password Pa$$w0rd.
2.Use Server Manager to install the DNS Server role.
PROHIBITED USE STUDENT .ONLY
Administering Windows Server® 2012 2-7
Considerations for Deploying the DNS Server Role |
MCT |
||||
When you are planning to deploy DNS, you |
|
||||
|
|
|
|||
|
USE |
||||
must review several considerations. Some of the |
|
||||
questions that you should ask include: |
|
||||
• How many DNS zones will you configure on |
|
||||
the server and how many DNS records will |
|
||||
each zone contain? Typically, zones map on |
|
||||
|
|
|
|||
a one-to-one basis with domains in your |
|
|
|
||
namespace. When you have a large number |
|
|
|
||
of records, it might make more sense to split |
|
|
|
||
the records into multiple zones. |
|
|
|
||
• How many DNS clients will be |
|
|
|
||
|
ONLY. |
||||
communicating with the server on which you |
|||||
configure the DNS role? The larger the number of client resolvers, the greater is the load placed on |
|||||
the server. When you anticipate additional load, consider deploying additional DNS servers. |
|||||
STUDENT |
|||||
• Where will you place DNS servers? For example, will you place the servers centrally, or does it make |
|||||
more sense to locate DNS servers in branch offices? If there are few clients at a branch office, you |
|||||
could satisfy most DNS requests by using a central DNS server or by implementing a caching-only |
|||||
server. A large number of users at a branch might benefit from a local DNS server with appropriate |
|||||
zone data. |
|
|
|||
How you answer the preceding questions will determine how many DNS servers you must deploy, and |
|||||
where you should place them. |
|||||
Active Directory Integration |
|||||
The Windows Server 2012 DNS role can store the DNS database in two different ways, as the following |
|||||
table shows. |
|
|
|||
|
|
|
|||
Storage method |
Description |
|
|
||
|
|
||||
|
|
|
|
|
|
Text File |
The DNS server role stores the DNS entries in a text file, which you can edit |
|
|
||
|
with a text editor. |
|
|
||
|
|
|
|
||
Active Directory |
The DNS server role stores the DNS entries in the Active Directory database, |
USE |
|||
|
which replicates to other domain controllers, even if they do not run the |
||||
|
|
|
|||
|
Windows Server 2008 DNS role. You cannot use a text editor to edit DNS data |
||||
|
|
|
|
||
|
|
|
PROHIBITED |
||
that Active Directory stores.
Typically, you will deploy the DNS role on all domain controllers. If you decide to implement some other
replication to transfer the zone to all other domain controllers. If you implement non-Active Directory

2-8 Configuring and Troubleshooting Domain Name System
Lesson 2
Configuring the DNS Server Role
The DNS infrastructure is the basis for name resolution on the Internet and in AD DS domains based on Windows Server 2012. This lesson provides guidance and information about what is required to configure the DNS server role, and explains the basic functions of a DNS server.
Lesson Objectives
After completing this lesson, you will be able to:
•List the components of a DNS solution.
•Describe how various types of DNS queries work.
•Describe DNS resource records.
•Explain how root hints work.
•Explain how forwarding and conditional forwarding works.
•Explain how DNS server caching works.
•Explain how to configure the DNS server role properties.
USE STUDENT .ONLY USE MCT
The DNS resolver generates and sends iterative or recursive queries to the DNS server. A DNS resolver can be any computer performing a DNS lookup that requires interaction with the DNS server. DNS servers also can issue DNS requests to other DNS servers.
PROHIBITED

Administering Windows Server® 2012 2-9
What Are DNS Queries? |
MCT |
||||
A DNS query is the method that you use to |
|
||||
|
|
|
|||
|
USE |
||||
request name resolution, and involves a query |
|
||||
being sent to a DNS server. There are two types |
|
||||
of responses to DNS queries: authoritative and |
|
||||
nonauthoritative. |
|
||||
It is important to note that DNS servers also can |
|
||||
|
|
|
|||
act as DNS resolvers and send DNS queries to |
|
|
|
||
other DNS servers. |
|
|
|
||
A DNS server can be either authoritative or |
|
|
|
||
nonauthoritative for the query’s namespace. A |
|
|
|
||
DNS server is authoritative when it hosts a primary |
|
|
|
||
|
ONLY. |
||||
or secondary copy of a DNS zone. The two types |
|||||
of queries are: |
|||||
• |
|
|
|||
An authoritative query is one for which the server can return an answer that it knows is correct, |
|
|
|||
|
because the request is directed to the authoritative server that manages the domain. |
|
|
||
• A DNS server that contains in its cache the domain being requested answers a nonauthoritative query |
|||||
|
by using forwarders or root hints. However, the answer provided might not be accurate, because only |
||||
|
the authoritative DNS server for the given domain can issue that information. |
|
|
||
If the DNS server is authoritative for the query’s namespace, the DNS server will check the zone, and then |
|||||
do one of the following: |
STUDENT |
||||
• Return the requested address. |
|||||
• Return an authoritative “No, that name does not exist.” |
|||||
|
Note: An authoritative answer can be given only by the server with direct authority for the |
||||
|
|||||
|
|||||
queried name. |
USE |
||||
If the local DNS server is nonauthoritative for the query’s namespace, the DNS server will do one of the |
|||||
following: |
|||||
• |
Check its cache, and return a cached response. |
||||
|
|
||||
• Forward the unresolvable query to a specific server known as a forwarder. |
|
|
|||
• Use well-known addresses of multiple root servers to find an authoritative DNS server to resolve the |
|||||
|
query. This process uses root hints. |
PROHIBITED |
|||
|
|
|
|||
Recursive Queries
A recursive query can have two possible results:
• It returns the IP address of the requested host.
• The DNS server cannot resolve an IP address.
For security reasons, it sometimes is necessary to disable recursive queries on a DNS server. This prevents the DNS server in question from forwarding its DNS requests to another server. This can be useful when you do not want a particular DNS server communicating outside its local network.

2-10 Configuring and Troubleshooting Domain Name System
Iterative Queries
is responsible for delivering mail for another
Iterative queries provide a mechanism for accessing domain-name information that resides across the |
MCT |
|||
DNS system, and enable servers to resolve names quickly and efficiently across many servers. |
||||
USE |
||||
When a DNS server receives a request that it cannot answer using its local information or its cached |
||||
lookups, it makes the same request to another DNS server by using an iterative query. |
||||
When a DNS server receives an iterative query, it might answer with either the IP address for the domain |
||||
name (if known) or with a referral to the DNS servers that are responsible for the domain being queried. |
||||
DNS Resource Records |
|
.ONLY |
||
The DNS zone file stores resource records. |
|
|
||
|
|
|||
Resource records specify a resource type and |
|
|
||
the IP address to locate the resource. The most |
|
|
||
common resource record is an A resource record. |
|
|
||
This is a simple record that resolves a hostname |
|
|
STUDENT |
|
to an IP address. The host can be a workstation, |
|
|
||
server, or another network device, such as a |
|
|
||
router. |
|
|
||
Resource records also help find resources for |
|
|
||
a particular domain. For instance, when an |
|
|
||
Exchange server needs to find the server that |
|
|
||
|
|
|
||
|
|
|
||
domain, it will request that domain’s Mail Exchanger (MX) record, which points to the A record of the host that is running the SMTP mail service.
Resource records also can contain custom attributes. MX records, for instance, have a preference attribute, which is useful if an organization has multiple mail servers. This will inform the sending server which mail server the receiving organization prefers. Service locator (SRV) records also contain information regarding
on which port the service is listening and the protocol that you should use to communicate with the USE service.
PROHIBITED

|
|
|
Administering Windows Server® 2012 2-11 |
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
DNS resource records |
Description |
|
MCT |
|||
|
|
|
|
|
|
|
|
|
AAAA |
The main record that resolves a host name to an IPv6 address. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Pointer (PTR) resource record |
The record is used to look up and map an IP address to a |
USE |
||||
|
|
domain name. The reverse lookup zone stores the names. |
|||||
|
|
|
|
||||
|
What Are Root Hints? |
|
|
||||
|
|
|
|
|
|
|
|
|
Root hints are the list of servers on the Internet |
|
|
|
|
|
|
|
ONLY. |
||||||
|
that your DNS server uses if it cannot resolve a |
|
|||||
|
DNS query by using a DNS forwarder or its own |
|
|||||
|
cache. The root hints are the highest servers in |
|
|||||
|
the DNS hierarchy and can provide the necessary |
|
|||||
|
information for a DNS server to perform an |
|
|||||
|
|
|
|
||||
|
iterative query to the next lowest layer of the |
|
|
|
|
|
|
|
DNS namespace. |
|
|
|
|
|
|
|
Root servers are installed automatically when |
|
|
|
|
|
|
|
you install the DNS role. They are copied from the |
|
|
|
|
|
|
|
cache.dns file that the DNS role setup files include. |
|
|
|
|
|
|
You also can add root hints to a DNS server to
support lookups for noncontiguous domains within a forest.
When a DNS server communicates with a root hints server, it uses only an iterative query. If you select the
Do Not Use Recursion For This Domain option, the server will not be able to perform queries on the |
STUDENT |
root hints. If you configure the server to use a forwarder, it will attempt to send a recursive query to its |
|
forwarding server. If the forwarding server does not answer this query, the server will respond that the |
|
host could not be found. |
It is important to understand that recursion on a DNS server and recursive queries are not the same thing. Recursion on a server means that the server will use its root hints and try to resolve a DNS query. The nextUSE topic discusses iterative and recursive queries in more detail.
PROHIBITED

2-12 Configuring and Troubleshooting Domain Name System |
MCT |
|
|
|
|
|
|
|
The server that is forwarding requests in the network must be able to communicate with the DNS server that is located on the Internet. This means that either you configure it to forward requests to another DNS server or it uses root hints to communicate.
A conditional forwarder is a configuration setting in the DNS server that forwards DNS queries according USEONLY to the query’s DNS domain name. For example, you can configure a DNS server to forward all queries that
it receives for names ending with corp.contoso.com to the IP address of a specific DNS server or to the IP addresses of multiple DNS servers. This can be useful when you have multiple DNS namespaces in a forest.
Use conditional forwarders if you have multiple internal namespaces. This provides faster name resolution..  STUDENTUSE
STUDENTUSE
The DNS client cache is a DNS cache that the DNS Client service stores on the local computer. To view the current client-side cache, run the ipconfig /displaydns command at the command prompt. If you must clear the local cache, such as when you are troubleshooting name resolution, you can use ipconfig /flushdns.
Note: You also can use the following Windows PowerShell® cmdlets:
PROHIBITED
•clear-DnsClientCache to delete the DNS resolver cache
•get-DnsClientCache to view the resolver cache
