
- •Table of Contents
- •Foreword
- •Do Not Pass GO
- •Counting in Martian
- •Octal: How the Grinch Stole Eight and Nine
- •Hexadecimal: Solving the Digit Shortage
- •From Hex to Decimal and from Decimal to Hex
- •Arithmetic in Hex
- •Binary
- •Hexadecimal as Shorthand for Binary
- •Switches, Transistors, and Memory
- •The Shop Foreman and the Assembly Line
- •The Box That Follows a Plan
- •DOS and DOS files
- •Compilers and Assemblers
- •The Assembly Language Development Process
- •DEBUG and How to Use It
- •Chapter 5: NASM-IDE: A Place to Stand Give me a lever long enough, and a place to stand, and I will move the Earth.
- •NASM-IDE's Place to Stand
- •Using NASM-IDE's Tools
- •NASM-IDE's Editor in Detail
- •Other NASM-IDE Features
- •The Nature of Segments
- •16-Bit and 32-Bit Registers
- •The Three Major Assembly Programming Models
- •Reading and Changing Registers with DEBUG
- •Assembling and Executing Machine Instructions with DEBUG
- •Machine Instructions and Their Operands
- •Reading and Using an Assembly Language Reference
- •Rally Round the Flags, Boys!
- •Using Type Specifiers
- •The Bones of an Assembly Language Program
- •Assembling and Running EAT.ASM
- •One Program, Three Segments
- •Last In, First Out via the Stack
- •Using DOS Services through INT
- •Boxes within Boxes
- •Using BIOS Services
- •Building External Libraries of Procedures
- •Creating and Using Macros
- •Bits Is Bits (and Bytes Is Bits)
- •Shifting Bits
- •Flags, Tests, and Branches
- •Assembly Odds 'n Ends
- •The Notion of an Assembly Language String
- •REP STOSW, the Software Machine Gun
- •The Semiautomatic Weapon: STOSW without REP
- •Storing Data to Discontinuous Strings
- •Chapter 12: The Programmer's View of Linux Tools and Skills to Help You Write Assembly Code under a True 32-Bit OS
- •Prerequisites-Yukkh!
- •NASM for Linux
- •What's GNU?
- •The make Utility and Dependencies
- •Using the GNU Debugger
- •Your Work Strategy
- •Genuflecting to the C Culture
- •A Framework to Build On
- •The Perks of Protected Mode
- •Characters Out
- •Characters In
- •Be a Time Lord
- •Generating Random Numbers
- •Accessing Command-Line Arguments
- •Simple File I/O
- •Conclusion: Not the End, But Only the Beginning
- •Where to Now?
- •Stepping off Square One
- •Notes on the Instruction Set Reference
- •AAA Adjust AL after BCD Addition
- •ADC Arithmetic Addition with Carry
- •ADD Arithmetic Addition
- •AND Logical AND
- •BT Bit Test (386+)
- •CALL Call Procedure
- •CLC Clear Carry Flag (CF)
- •CLD Clear Direction Flag (DF)
- •CMP Arithmetic Comparison
- •DEC Decrement Operand
- •IMUL Signed Integer Multiplication
- •INC Increment Operand
- •INT Software Interrupt
- •IRET Return from Interrupt
- •J? Jump on Condition
- •JMP Unconditional Jump
- •LEA Load Effective Address
- •MOV Move (Copy) Right Operand into Left Operand
- •NOP No Operation
- •NOT Logical NOT (One's Complement)
- •OR Logical OR
- •POP Pop Top of Stack into Operand
- •POPA Pop All 16-Bit Registers (286+)
- •POPF Pop Top of Stack into Flags
- •POPFD Pop Top of Stack into EFlags (386+)
- •PUSH Push Operand onto Top of Stack
- •PUSHA Push All 16-Bit GP Registers (286+)
- •PUSHAD Push All 32-Bit GP Registers (386+)
- •PUSHF Push 16-Bit Flags onto Stack
- •PUSHFD Push 32-Bit EFlags onto Stack (386+)
- •RET Return from Procedure
- •ROL Rotate Left
- •ROR Rotate Right
- •SBB Arithmetic Subtraction with Borrow
- •SHL Shift Left
- •SHR Shift Right
- •STC Set Carry Flag (CF)
- •STD Set Direction Flag (DF)
- •STOS Store String
- •SUB Arithmetic Subtraction
- •XCHG Exchange Operands
- •XOR Exclusive Or
- •Appendix C: Web URLs for Assembly Programmers
- •Appendix D: Segment Register Assumptions
- •Appendix E: What's on the CD-ROM?
- •Index
- •List of Figures
- •List of Tables

The Three Major Assembly Programming Models
I mentioned earlier that there are three major programming models that you might encounter in assembly language work. The differences between them lie (mostly) in the use of registers to address memory. (And the other differences, especially on the high end, are for the most part hidden from you by the operating system.) In this section I'm going to lay out the three models, all of which we'll touch on throughout the course of the rest of this book.
Real Mode Flat Model
In real mode, if you recall, the CPU can see only 1 megabyte (1,048,576) of memory. You can access every last one of those million-odd bytes by using the segment:offset trick shown earlier to form a 20-bit address out of two 16-bit addresses. Or...you can be content with 64K of memory, and not fool with segments at all.
In the real mode flat model, your program and all the data it works on must exist within a single 64K block of memory. Sixty-four kilobytes! Pfeh! What could you possibly accomplish in only 64K bytes? Well, the first version of WordStar for the IBM PC fit in 64K. So did the first three major releases of Turbo Pascal-in fact, the Turbo Pascal program itself occupied a lot less than 64K because it compiled its programs into memory. The whole Turbo Pascal package-compiler, text editor, and some odd toolscame to just over 39K. Thirty-nine kilobytes! You can't even write a letter to your mother (using Microsoft Word) in that little space these days!
True, true. But that's mostly because we don't have to. Memory's gotten cheap, and our machines now contain what by historical standards is an enormous amount of it. So we've gotten lazy and hoggish and wasteful, simply because we can get away with it.
But if you take pains to make effective use of memory, you can do spectacular things in 64K. Certainly, for your first simple steps in assembly language programming, you won't need anything near 64K-and the simplicity of the model will make it much easier to become familiar with the machine instructions you'll use to write your programs. Finally, real mode flat model is the "little brother" of protected mode flat model, which is the code model you use when programming under Linux. If you learn the ways of real mode flat model, protected mode flat model will be a snap. (All the trouble you'll have won't be with assembly code or memory models, but with the byzantine requirements of Linux itself.)
The real mode flat model is shown diagrammatically in Figure 6.8. There's not much to it. The segment registers are all set to point to the beginning of the 64K block of memory you can work with. (The operating system sets them when it loads and runs your program.) They all point to that same place and never change as long as your program is running. That being the case, you can simply forget about them. Poof! No segment registers, no fooling with segments, and none of the ugly complication that comes with them.
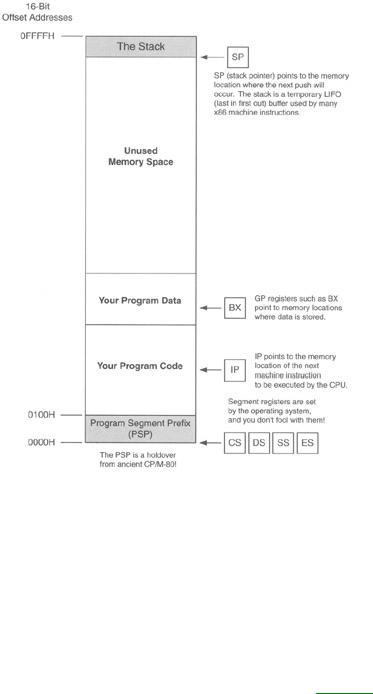
Figure 6.8: The real mode flat model.
Because a 16-bit register such as BX can hold any value from 0 to 65,535, it can pinpoint any single byte within the full 64K your program has to work with. Addressing memory can thus be done without the explicit use of the segment registers. The segment registers are still functioning, of course, from the CPU's point of view. They don't disappear and are still there, but the operating system sets them to values of its own choosing when it launches your program, and those values will be good as long as the program runs. You don't have to access the segment registers in any way to write your program.
Most of the general-purpose registers may contain addresses of locations in memory. You use them in conjunction with machine instructions to bring data in from memory and write it back out again.
At the top of the single segment that your program exists within, you'll see a small region called the stack. The stack is a LIFO (last in, first out) storage location with some very special uses. I explain what the stack is and how it works in considerable detail in Chapter 8.
Real mode flat model is the programming model we'll use for our first several example programs.
Real Mode Segmented Model
The first two editions of this book focused entirely on real mode segmented model, which was the mainstream programming model throughout the MS-DOS era, and still holds true when you boot your Windows 9x machine into MS-DOS mode, or launch an MS-DOS window. It's a complicated, ugly system that requires you to remember a lot of little rules and gotchas. I'm still going to teach it here, because some people may still wish to write code to run under MS-DOS, and also because it illustrates the use of segments very clearly. (Under real mode flat model you can squint a little and pretend that segments don't really exist.)
In real mode segmented model, your program can see the full 1MB of memory available to the CPU in real mode. It does this by combining a 16-bit segment address with a 16-bit offset address. It doesn't just glom them together into a 32-bit address, however. You need to think back to my discussion of segments earlier in this chapter. A segment address is not really a memory address. A segment

address specifies one of the 65,535 slots at which a segment may begin. One of these slots exists every 16 bytes from the bottom of memory to the top. Segment address 0000H specifies the first such slot, at the very first location in memory. Segment address 0001H specifies the next slot, which lies 16 bytes higher in memory. Jumping up-memory another 16 bytes gets you to segment address 0002H, and so on. You can translate a segment address to an actual 20-bit memory address by multiplying it by 16. Segment address 0002H is thus equivalent to memory address 0020H, which is the 32nd byte in memory.
But such multiplication isn't something you have to do. The CPU handles the combination of segments and offsets into a full 20-bit address. Your job is to tell the CPU where the two different components of that 20-bit address are. The customary notation is to separate the segment register and the offset register by a colon. For example:
SS : SP
SS : BP
ES : DI
DS : SI
CS : BX
Each of these five register combinations specifies a full 20-bit address. ES:DI, for example, specifies the address as the distance in DI from the start of the segment called out in ES.
I've drawn a diagram outlining real mode segmented model in Figure 6.9. In contrast to real mode flat model (shown in Figure 6.8), the diagram here shows all of memory, not just the one little 64K chunk that your real mode flat model program is allocated when it runs. A program written for real mode segmented model can see all of real mode memory.
Figure 6.9: The real mode segmented model.
The diagram shows two code segments and two data segments. In practice you can have any reasonable number of code and data segments, not just two of each. You can access two data segments at the same time, because you have two segment registers available to do the job: DS and ES. Each can specify a data segment, and you can move data from one segment to another using any of several machine instructions. (We speak more of this in later chapters.) However, you only have one

code segment register, CS. CS always points to the current code segment, and the next instruction to be executed is pointed to by the IP register. You don't load values directly into CS to change from one code segment to another. Machine instructions called jumps change to another code segment as necessary. Your program can span several code segments, and when a jump instruction (there are several kinds) needs to take execution into a different code segment, it changes the value in CS for you.
There is only one stack segment for any single program, specified by the stack segment register SS. The stack pointer register SP points to the memory address (relative to SS, albeit in an upside-down direction) where the next stack operation will take place. The stack will require some considerable explaining, which I take up in Chapter 8.
You need to keep in mind that in real mode, there will be pieces of the operating system (and if you're using an 8086 or 8088, that will be the whole operating system) in memory with your program, along with important system data tables. You can destroy portions of the operating system by careless use of segment registers, which will cause the operating system to crash and take your program with it. This is the danger that prompted Intel to build new features into its 80386 and later CPUs to support a protected mode. In protected mode, application programs (that is, the programs that you write, as opposed to the operating system or device drivers) cannot destroy the operating system nor other applications programs that happen to be running elsewhere in memory in a multitasking system. That's what the protected means.
(Yes, it's true that there is a sort of rudimentary protected mode present in the 80286, but no one ever really used it and it's not much worth discussing today.)
Protected Mode Flat Model
Intel's CPUs have implemented a very good protected mode architecture since the 386 appeared in 1986. However, application programs cannot make use of protected mode by themselves. The operating system must set up and manage a protected mode before application programs can use it. MS-DOS couldn't do this, and Microsoft Windows couldn't really do it either until Windows NT first appeared in 1994.
Other protected mode operating systems have since appeared. The best known is probably Linux, the implementation of Unix written from scratch by a young Finnish college student during the first half of the 1990s. Windows NT and Linux are vying for the same general market, and while NT will probably remain the market leader for years to come, Linux is showing surprising strength for something that no one organization actually owns in the strictest sense of the word.
Protected mode assembly language programs may be written for both Windows NT and Linux. The easiest way to do it under NT is to create console applications, which are text-mode programs that run in a text-mode window called a console. The console is controlled through a command line almost identical to the one in MS-DOS. Console applications use protected mode flat model and are fairly straightforward compared to writing Windows applications. The default mode for Linux is a text console, so it's even easier to create assembly programs for Linux, and a lot more people appear to be doing it. The memory model is very much the same.
I've drawn the protected mode flat model in Figure 6.10. Your program sees a single block of memory addresses running from zero to a little over 4 gigabytes. Each address is a 32-bit quantity. All of the general-purpose registers are 32 bits in size, and so one GP register can point to any location in the full 4-GB address space. The instruction pointer is 32 bits in size as well, so EIP can indicate any machine instruction anywhere in the 4 GB of memory.

Figure 6.10: The protected mode flat model.
The segment registers still exist, but they work in a radically different way. Not only don't you have to fool with them; you can't. The segment registers are now to be considered part of the operating system, and in most cases you can neither read nor change them directly. Their new job is to define where your 4GB memory space exists in physical or virtual memory. If these terms mean nothing to you, don't fretyou'll pick them up over time, and I don't have the space to explain them in detail here.
It's enough to understand that when your program runs, it receives a 4-GB address space in which to play, and any register can potentially address any of those 4 billion memory locations, all by itself. Not all of the 4 GB is at your program's disposal, and there are certain parts of the memory space that you can't use or even look at. Unfortunately, the rules are specific to the operating system you're running under, and I can't generalize too far without specifying Linux or Windows NT or some other protected mode OS.
But it's worth taking a look back at Figure 6.8 and comparing real mode flat model to protected mode flat model. The main difference is that in real mode flat model, your program owns the full 64K of memory that the operating system hands it. In protected mode flat model, you are given a portion of 4 GB of memory as your own, while other portions will still belong to the operating system. Apart from that, the similarities are striking: A general-purpose (GP) register by itself can specify any memory location in the full memory address space, and the segment registers are really the tools of the operating system and not you the programmer. (Again, in protected mode flat model, a GP register can hold the address of any location in its 4-GB space, but attempting to actually read or write certain locations will be forbidden by the OS and will trigger an error.)
Note well that we haven't really talked about machine instructions yet, and we've been able to pretty crisply define the universe in which machine instructions exist and work. Memory addressing and registers are key in this business. If you know them, the instructions will be a snap. If you don't know them, the instructions won't do you any good!
What difficulty exists in programming for protected mode flat model lies in understanding the operating system, its requirements, and its restrictions. This can be a substantial amount of learning: Windows NT and Linux are major operating systems that can take years of study. I'm going to introduce you to protected mode assembly programming in flat model later in this book, but you're going to have to learn the operating system on your own. This book is only the beginning-there's a long road out there to be walked, and you're barely off the curb.
