
Hacking Wireless Networks For Dummies
.pdf
40 |
Part I: Building the Foundation for Testing Wireless Networks |
see what can be found from a hacker’s point of view. You may be able to gather more information, capture data out of thin air with a sniffer, or determine that a specific patch is missing.
Remember not to discount what you’ve already found simply because you’re just now getting to the formal “vulnerability assessment” portion of the testing. Even without poking and prodding your wireless systems further, you may already have discovered some juicy vulnerabilities (such as default SSIDs, WEP not being enabled, and critical servers being accessible through the wireless network).
You can look for these vulnerabilities in two ways: manually and automatically. The next two sections discuss these two methods in greater detail.
Manual assessment
The first way — manual assessment — is the most time-consuming, but it’s essential. Manually assessing vulnerabilities can be difficult at first, but it does get easier with experience. We call this assessment manual, but it often involves various semiautomatic security tools that don’t just perform a run-of- the-mill robo-assessment but need your guiding hand now and then. Knowing how wireless networks and their associated operating systems and software work — knowing what’s right and what stands out as a potential problem — can really help out your manual assessments. Be sure to check out Peter’s book Wireless Networks For Dummies (as well as the other Linux and Windows For Dummies titles from Wiley) to learn more about these systems. Chey Cobb’s book Network Security For Dummies is also a great resource to give you a handle on a wide variety of information-security concepts. Manual vulnerability-assessment techniques are a must — and we’ll outline various ways to do them in various chapters throughout this book.
Automatic assessment
The second way of looking for vulnerabilities is to use an automated tool such as the open source Nessus (www.nessus.org) or the commercial LANguard Network Security Scanner (www.gfi.com/lannetscan) or QualysGuard. These tools can automate the vulnerability-assessment process by scanning live systems and determining whether vulnerabilities (actual or potential) exist. These tools take a lot of the legwork out of vulnerability assessment, giving you more time to spend catching up on e-mails or watching Seinfeld reruns. We can’t imagine performing automated ethical-hacking tests without these tools.

Chapter 3: Implementing a Testing Methodology |
41 |
There are many excellent wireless-hacking tools that you won’t have to spend a dime on. They work great for running specific tests — but when it comes time to take a broader look at vulnerabilities, these commercial tools prove their worth. When you’re delicately probing the operating systems and applications running on your wireless network, you definitely get what you pay for.
Finding more information
After you or your tools find suspected vulnerabilities, there are various wireless security vulnerability resources you can peruse to find out more information on the issues you find. A good place to start is your wireless vendor’s Web site. Look in the Support or Knowledgebase section of the Web site for known problems and available security patches. You can also peruse the following vulnerability databases for in-depth details on specific vulnerabilities, how they can be exploited, and possible fixes:
US-CERT Vulnerability Notes Database (www.kb.cert.org/vuls)
NIST ICAT Metabase (http://icat.nist.gov/icat.cfm)
Common Vulnerabilities and Exposures (http://cve.mitre.org/cve)
Another good way to get more information on specific security issues is to do a Google Web and groups search. Here you can often find other Web sites, message boards, and newsgroups where people have posted problems and (hey, let’s be optimistic) solutions about your particular issue.
Penetrating the System
After you map your network, see which systems are running what, and find specific vulnerabilities, there’s one more phase in your ethical-hacking methodology — if you choose to pursue it. This is the system-penetration phase: actually getting in. This is the true test of what systems and information can actually be compromised on your wireless network and the ultimate goal of malicious hackers.
Penetrating your wireless systems simply means acting as if you were completely unauthorized to access the resources on your wireless network — and trying to get in anyway. Sure, you’ve already been able to connect to your network “as an outsider” thus far, but this is where you take it all the way — by joining the wireless network, connecting to various systems, and doing things such as

42 |
Part I: Building the Foundation for Testing Wireless Networks |
Logging in to the network
Browsing the Internet
Sending and receiving e-mails
Changing AP configuration settings
Capturing network data using a sniffer such as ethereal (www.ethereal. com) or AiroPeek
Mapping to network drives
Editing, copying, and deleting files — just be careful which ones!
The hackers are doing these things, so it may make sense to try them yourself so you can get a true view of what’s possible on your network.
If you choose to penetrate your systems, proceed with caution — and work slowly and carefully to minimize any disruptions you may create!
In Parts II and III of this book, we outline how you can perform the tests we’ve described in this ethical-hacking methodology so you can start putting these procedures to work for you!

Chapter 4
Amassing Your War Chest
In This Chapter
Choosing your platform: PDAs versus laptops
Choosing your software
Using software emulators
Choosing transceivers, antennae, and GPS
Signal jamming
Acyberwar is being waged. Your perimeter is under siege. What makes the attack especially insidious is that you cannot see your enemy. This
isn’t hand-to-hand combat. Your enemy could be 2 miles from your office and still access your network and data. Your access point is your first line of defense in this war. It behooves you, then, to prepare for battle.
One way to prepare for any war is to participate in war games. Real war games allow you to test your equipment, tactics, and operations. In this case, war games allow you to test your wireless networks under normal conditions. Like the Reservist going off to war, you also must receive adequate training on the latest weapons and tactics. Although the rest of the book focuses on tactics, this chapter focuses on equipment. You need practice with the tools the crackers use for real.
You need some hardware and software, but you have choices about what type of hardware and software you use. This chapter serves as your armory. If you favor the Windows platform, we have some tools for you. Should you favor Linux, you will find some tools as well. We don’t leave Apple enthusiasts out; we have something for you, too.

44 |
Part I: Building the Foundation for Testing Wireless Networks |
Choosing Your Hardware
What’s your poison? Laptop or personal digital assistant? The two primary hardware platforms for wireless hacking are
Personal digital assistant (PDA) or personal electronic device (PED)
Portable or laptop
Each platform has its pros and cons. First, a PDA is readily portable so you can easily carry it from place to place. However, you won’t find as many tools for the PDA as you will for other platforms — depending on the operating system you run on your handheld device. If you run the Zaurus operating system, for example, you have more choices for software than you do if you choose the Pocket PC operating system.
One thing is safe to say: You don’t want to run wireless-hacking tools on a desktop. You may want to store NetStumbler files on the desktop, but the desktop is not really portable. The key thing to think about when choosing your hardware is portability. When performing hacking tests, you must be able to walk around your office building or campus, so a desktop is probably not the best choice. However, we know of people who use mini-towers in their cars for wardriving (discussed later in this chapter), but we don’t recommend it!
The personal digital assistant
Because of its portability, a PDA is the perfect platform for wardriving — but not for tasks requiring processing power. You want to get a PDA that uses either the ARM, MIPS, or SH3 processor. We recommend the Hewlett-Packard iPAQ (ARM processor), the Hewlett-Packard Jornada (SH3 processor), or the Casio MIPS for wardriving. These are handy devices since someone was kind enough to develop network discovery software for these platforms.
ARM’s processor technology has been licensed by more than 100 parties, so you should easily find a solution you like. It’s so easy, in fact, that you would better spend your time choosing the right operating system for your needs. We tell you more about operating systems in the software section of this chapter.
The portable or laptop
PDAs are great, but, typically, ethical hackers use laptops. Laptops have dropped dramatically in price the last few years, so they have become more accessible. You don’t need a lot of processing power, but, to paraphrase Tim

Chapter 4: Amassing Your War Chest |
45 |
Allen, more power is better. You can use almost any operating system, including Windows 98, although you will find you get better results when using a newer and supported operating system. In addition to the laptop, you need the following components to get maximum results from your ethical hacking:
Hacking software
A wireless network interface card (NIC) that can be inserted into your laptop — preferably one with an external antenna jack
External antenna (directional or omnidirectional) with the proper pigtail cable to connect your external antenna to your wireless NIC
Portable global positioning system (GPS)
DC power cable or DC to AC power inverter to power your laptop from your car’s 12-volt DC cigarette lighter plug socket. These are widely available from RadioShack, Kmart, Staples, CompUSA, or Wal-Mart stores.
The next few sections discuss these components in greater detail.
Hacking Software
To do your job properly, you need a selection of freeware and commercial software. Fortunately, a glut of freeware programs is available, so you don’t need a champagne budget; a beer budget should suffice. In fact, if you are prepared to run more than one operating system, you can get by using only freeware tools. You need the following software to do all the hacking exercises in this book:
Partitioning or emulation software
Signal strength–testing software
Packet analyzer
Wardriving software
Password crackers
Packet injectors
Using software emulators
In a perfect world, all the tools available would work on the same operating system. But in the real world, that’s not the case. Many great tools operate on operating systems that are incompatible with each other. Very few of us, of course, are conversant with multiple operating systems. Also, few of us have

46 |
Part I: Building the Foundation for Testing Wireless Networks |
the money to support duplicate hardware and software. So, how can you use all these tools? You need to find a solution that allows you to run more than one operating system on the same machine.
To solve this problem, people often build dual-boot or multi-boot workstations. You can use a product like Symantec’s PartitionMagic (www.symantec.com/ partitionmagic) to set up partitions for the various operating systems. For more information about setting up and using PartitionMagic, among other things, check out Kate Chase’s Norton All-in-One Desk Reference For Dummies
(Wiley). After you set up your partitions, you install the operating systems on the various partitions.
When everything’s installed, you can select the operating system you want to use when you boot the system. Say you’re using NetStumbler on Windows XP and you decide to use WEPcrack — which is available only on Linux — on the access points you just identified with NetStumbler. You shut down Windows XP, reboot your system, and select the Red Hat Linux operating system. When you want to use Windows XP again, you must do the reverse. This isn’t a bad solution, but flipping back and forth a lot eats up valuable time. And managing your partitions and trying to make the operating systems coexist on the same hardware can be challenging.
Enter software emulators. Software emulators allow you to emulate a guest operating system by running it on top of a host operating system. You can run Linux emulation on a Windows host, and vice versa. To emulate Windows or DOS on a Linux host, you can choose one of the following Windows-based emulators:
Bochs (http://bochs.sourceforge.net)
DOSEMU (www.dosemu.org)
Plex86 (http://savannah.nongnu.org/projects/plex86)
VMware (www.vmware.com)
WINE (www.winehq.com)
Win4Lin (www.netraverse.com)
Alternatively, you can emulate Linux on a Windows host. To do this, choose one of the following Linux-based emulators:
Cygwin (http://cygwin.com)
VMware (www.vmware.com)
Chapter 4: Amassing Your War Chest |
47 |
Mac lovers can already run most of the UNIX tools under the Mac OS. To emulate the Windows environment, you can run an emulator like Microsoft Virtual PC (www.microsoft.com/mac/products/virtualpc/virtualpc. aspx?pid=virtualpc).
To get you going, the next two sections discuss Cygwin and VMware, two excellent examples of emulation software.
Setting up Cygwin
Do you use Windows but have software that only runs on Linux? If so, Cygwin is your answer. Cygwin is a contraction of Cygnus + Windows. It provides a UNIX-like environment consisting of a Windows dynamically linked library (cygwin1.dll). Cygwin is a subsystem that runs on Windows and intercepts and translates UNIX commands. This is transparent to the user. With Cygwin, you can have the experience of running xterm and executing ls commands without ever leaving your safe Windows environment.
First, download Cygwin by going to http://cygwin.com. Installing Cygwin is easy when you follow these steps:
1.On the home page, click the Install or Update Now! (Using setup.exe) link about halfway down the page.
You see a File Download – Security Warning window.
2.Click Run to download Cygwin.
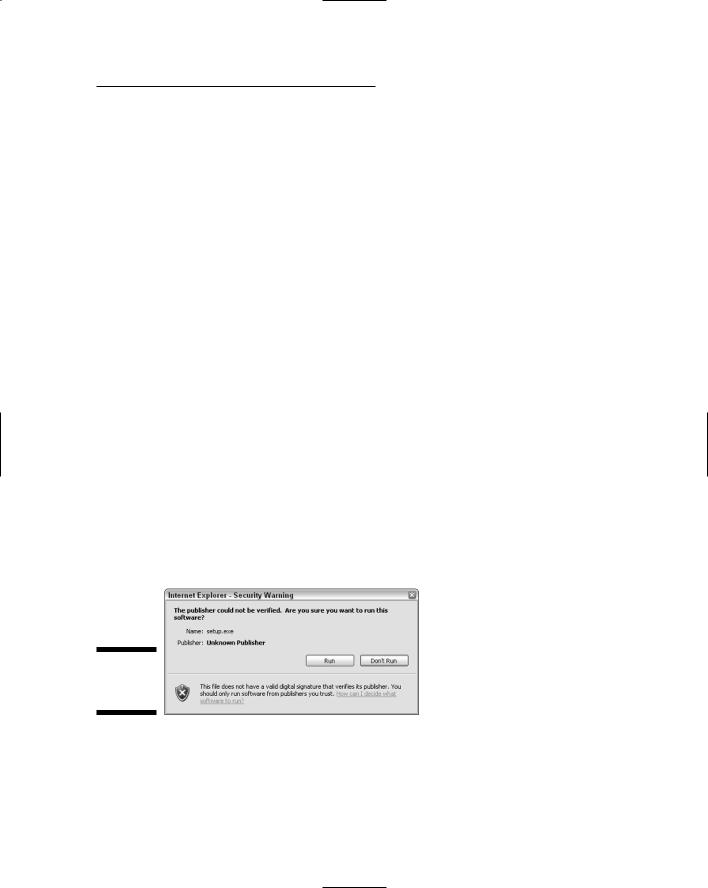
You see the message shown in Figure 4-1.
3.Click Run to run setup.exe.
You see the Cygwin Setup window shown in Figure 4-2.
Figure 4-1:
Security warning.
4. Click Next.

48 |
Part I: Building the Foundation for Testing Wireless Networks |
Figure 4-2:
Cygwin
setup.
5.Select Install from Internet and click Next.
This is the installation type. If you have a CD-ROM with Cygwin, select Install from Local Directory instead.
The Choose Installation Directory dialog box appears, as shown in Figure 4-3.
Figure 4-3:
Choosing the installation directory.
6.Choose the installation directory options based on your needs and setup and then click Next.
After installation, this is the Cygwin root directory. Leave the default or click Browse to select another location. You can decide whether to make Cygwin available to all users or just to you. In addition, you can decide whether you want DOS or UNIX file types.

Chapter 4: Amassing Your War Chest |
49 |
The ^M character
Ever see a ^M character at the end of your text files? Yes? Well, this likely means that someone transferred the file from UNIX to Windows using
binary format rather than ASCII. DOS file lines end with a newline and a carriage return while UNIX file lines end with the newline only.
7.Select a location in which to store the installation files. Then click Next.
Unless you have a compelling reason for not doing it, use the default. If you must put the installation files somewhere else, click Browse and select the location.
8.Select the type of Internet connection you have. Click Next.
We suggest that when you aren’t sure what to select here, use the default. If you’re doing this from your home office, then Direct Connection should work. If you’re at work, you might have a proxy server. If you have a proxy server, it’s perhaps best to talk to your system administrator.
9.Select a download site from the scroll box. Click Next.
You may have to try a few download sites before you find one that works for you. Peter tried several times to find a site. Either it would not start the download and required him to select a new site or it got halfway through the download and quit. You must persevere. Cygwin is worth it.
The Select Packages window appears, as shown in Figure 4-4.
Figure 4-4:
Selecting the packages to install.
