
- •Table of Contents
- •Preface
- •More than Just Email
- •Introducing Zimbra
- •What's in a Name?
- •Building Better Collaboration
- •Front-End
- •Back-End
- •The Benefits of Zimbra
- •Summary
- •Before the Installation
- •Hardware
- •Software
- •Editing the HOSTS File
- •Configuring DNS
- •Turning Off Sendmail
- •Installing on Red Hat Enterprise Linux 4
- •Installing the Red Hat Operating System
- •Installing Zimbra Collaboration Suite
- •Installing on SUSE ES 9
- •Preparing SUSE ES 9 for Zimbra
- •Installing on MAC OS X
- •Preparing MAC OS X Server for Zimbra
- •Installing the Zimbra Collaboration Suite
- •Post-Installation Steps
- •Configuring the Firewall
- •Uninstalling Zimbra
- •Summary
- •An Overview of the Administration Console
- •A. Content Pane
- •B. Search Bar
- •C. Monitoring
- •Server Management
- •Creating a New Domain
- •Configuring Global Settings
- •Class of Service
- •User Management
- •Creating User Accounts
- •Creating an Alias
- •Creating a Distribution List
- •Administering Zimbra from the Command Line
- •Managing Services with zmcontrol
- •Creating Accounts with zmprov
- •Summary
- •The Web Client System Requirements
- •A Bird's Eye View of the Web Client
- •Working with Email
- •Checking Email
- •Composing Email
- •Tags
- •Conversations
- •Managing Contacts
- •Sharing Address Books
- •Managing Schedules
- •Adding Appointments
- •Creating Multiple Calendars
- •Sharing Calendars
- •The Zimbra Documents
- •Creating Documents Pages
- •Sharing Documents
- •Saving Time with the Zimbra Assistant
- •Saving Even More Time with Keyboard Shortcuts
- •Sending an Email with Shortcuts
- •Summary
- •Built-In Security
- •Web Client Security
- •Mail Transfer Agent
- •Anti-Spam
- •Anti-Virus
- •Securing the Operating System
- •Host-Based Firewall
- •Services
- •Updates and Patching
- •Securing the Network
- •Firewalls
- •Virtual Private Networks
- •Summary
- •Exploring User Options
- •General Options
- •Mail Options
- •Mail Filters
- •Address Book
- •Calendar
- •Shortcuts
- •Configuring POP Accounts
- •Configuring Mail Identities
- •Building Searches
- •Building Our Search
- •Using a Saved Search
- •Summary
- •The PST Import Wizard
- •The Zimbra Connector for Outlook
- •A Look at Zimbra Integration
- •Contacts
- •Appointments
- •Sharing Outlook Folders
- •Summary
- •Preparing the Zimbra Server for Zimbra Mobile
- •Configuring Windows Mobile to Sync with Zimbra
- •Configuring Palm OS to Sync with Zimbra
- •Summary
- •An Overview of Zimlets
- •Mouse-Over Zimlet Example
- •The Date Zimlet
- •The Yahoo! Maps Zimlet
- •Managing Zimlets
- •Managing Zimlets through the Administrator Console
- •Assigning Zimlets to a COS
- •Assigning Zimlets to an Account
- •A Look at Configuring the RSS Zimlet
- •The RSS Zimlet in Action
- •Allowing RSS Feeds for Additional Sites
- •Managing Backups
- •Restoring Mailboxes
- •Using the Command Line for Backups
- •Summary
- •The Need for Monitoring
- •Availability
- •Scalability
- •Security
- •Working with Mail Queues
- •Monitoring Log Files
- •Summary
- •Index

This material is copyright and is licensed for the sole use by Kliwon Klimis on 28th October 2008 425 cilce, , frood, grradt, 525254
Securing Zimbra
Host-Based Firewall
When we first prepared the operating system for our initial Zimbra install (in Chapter 2), we looked at opening ports in our system, or host-based, firewall. During the initial install, the firewall was disabled. After Zimbra was successfully installed, we did an initial lockdown of our system by enabling the firewall and opening up all ports that were particular to Zimbra.
It is imperative to keep in mind one simple fact about ports, only open up ports that are necessary for your server to function. Any other ports should be blocked on the host. That being said, let's review the ports we opened up for Zimbra, and decide if there are a few we should go ahead and close. The list below is the same one from Chapter 2 listing the ports.
•https:tcp
•3930:tcp
•pop3:tcp
•imap:tcp
•imaps:tcp
•ldap:tcp
•pop3s:tcp
•7025:tcp
•5800:tcp
•5900:tcp
•7071:tcp
•3895:tcp
•3894:tcp
•ssh:tcp
Based on the Classes of Service (COS) that we have created this far and the features we have enabled, it is apparent the following ports are not needed or being used.
1.We disabled access to POP email. Therefore, we could remove the pop3:tcp and pop3s:tcp from our list of open ports.
2.We also are not allowing imap access to our server at this time. So we may go ahead and disable imap:tcp and imaps:tcp.
One other thing to consider is, will you be allowing access to the admin console over the public internet, or will it require local or VPN access. I would recommend not allowing access to the console, unless the request is coming from the local LAN (or VPN of course), that being said we could also disable 7071:tcp.
[ 126 ]
This material is copyright and is licensed for the sole use by Kliwon Klimis on 28th October 2008 425 cilce, , frood, grradt, 525254
Chapter 5
The rest of the ports we should keep active for our Zimbra server to work correctly.
Once all of the changes have been made, it would be a good idea to restart the firewall and Zimbra services to make sure all is functioning as it should.
Services
The same rule of the thumb for ports applies to services. If a service is running on your server that is not necessary, disable it. In the case above, we had already
determined we are not allowing POP3 and IMAP. Those we have not disabled, but using them is not allowed in the definitions of our COS.
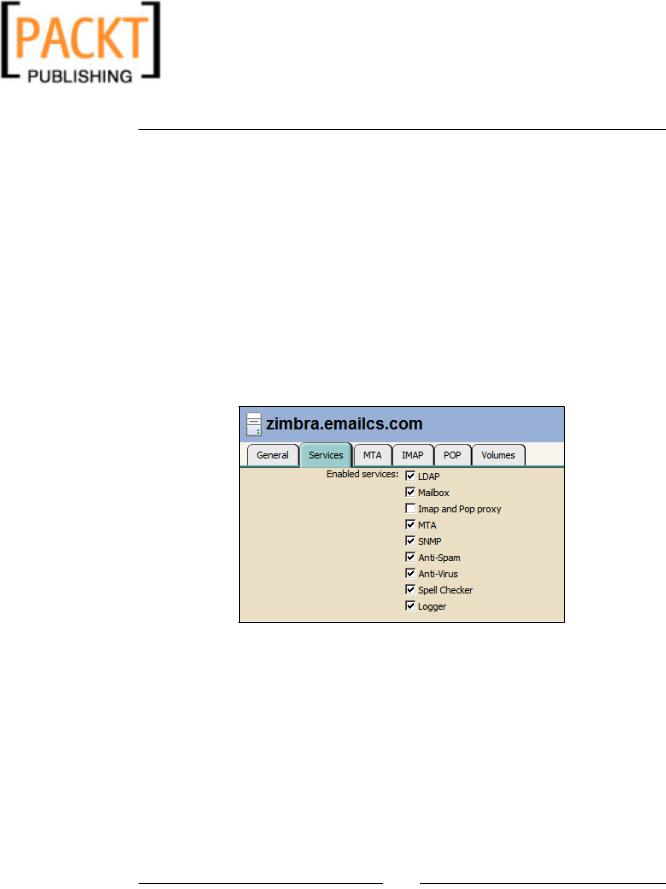
To determine which services Zimbra will start automatically, we need to open up the admin console and click on Servers in the Navigation Pane; then select your server and click on the Services tab. As shown in the following screenshot, any service with a check mark next to it will start up with Zimbra.
Besides Zimbra services, operating systems have a tendency to install services by default. These services may include sendmail, DNS, mySQL or other database, Apache, Squid, Webmin, whatever the case may be. If you are not using a service, disable it.
Updates and Patching
Running software updates and patches is critical for any server, and workstation for that matter, in your environment. Patches are used to fix vulnerabilities and bugs in software programs, and in the operating system itself. By not patching, you are leaving your server open to unnecessary risk.
[ 127 ]
